近年,IBM同Google等公司嘅突破令量子計算由理論漸漸成為現實,令加密貨幣圈對這項技術嘅討論再度升溫。IBM最新量子處理器已經有超過400個量子位,公司表示有「清晰路線圖」可以喺今個十年內實現全面量子運算。Google亦同樣樂觀,指大型量子計算剩下嘅工程問題「可以克服」,發展更係一日千里。
呢個進展已經引起加密貨幣界注意:論壇同專家討論緊量子電腦幾時會強到足以威脅支撐比特幣同其他區塊鏈嘅加密技術。有啲人,例如Solana聯合創辦人Anatoly Yakovenko,仲警告話到2030年出現重大量子突破嘅機會「一半一半」,促請比特幣社群「加快腳步」做好防護。不過亦有學者質疑,認為真正「有用」嘅量子電腦可能仲要15至20年先至見到,就好似NVIDIA行政總裁Jensen Huang最近所講。
可以肯定嘅係,量子運算已唔再係遙不可及嘅抽象概念,而係一個對網絡安全影響深遠嘅新技術。對加密貨幣世界嚟講,這既有威脅,亦有機遇。一方面,當量子電腦發展足夠先進,就可以攻破現時保障數碼資產嘅「不可破解」密碼學。另一方面,為對抗量子電腦而推動嘅「量子抗性加密」創新,反而可能令適應得及時嘅區塊鏈生態更堅韌。
本文將全面分析:點解量子運算對加密貨幣構成獨特威脅、佢可以點樣破解比特幣加密、專家預計咗幾時會發生(或唔會發生)、業界而家做緊啲乜嘢準備。我哋亦會探討假設性場景 —— 例如如果比特幣明天被量子攻擊會點 —— 以及長遠影響:邊啲人會得益,邊啲人會受損,「不可破解」變成「可破解」後加密經濟會點變。
重要的是,呢篇唔係危言聳聽。只係一個務實檢視潛在未來風險 —— 或許仲有好幾年甚至幾十年,但今日就要開始未雨綢繆。了解風險但唔被炒作牽着走,開發者同用戶而家就可以行多一步,確保當量子計算真正普及時,加密生態系統能夠適應唔會瓦解。
量子電腦點運作(去除浮誇成分)
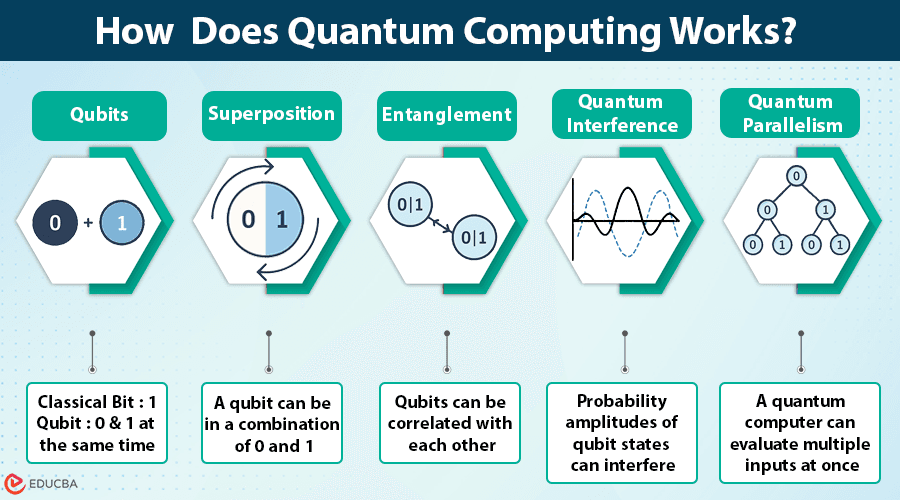
量子計算本質上同今日用開嘅傳統電腦完全唔同。傳統電腦用二進位bit(0或1);量子電腦就用量子位(qubits),可以同時擁有多種狀態,得益於「疊加」現象。簡單嚟講,qubit就好似一枚拋緊嘅硬幣 —— 唔單止係正面或反面,而係同時兩樣,直到觀察為止。qubit之間亦可以產生「糾纏」效應,即使隔開好遠,一個qubit嘅狀態都會影響另一個。咁樣量子電腦就可以一次過處理天文數字咁多種組合。只要組合夠多個qubit,再精確咁控制佢哋嘅機率波,就可以比傳統電腦快得多完成某些運算。
講量子電腦時經常聽到一啲術語。例如「量子霸權」(quantum supremacy),意思係量子電腦做咗啲傳統電腦無辦法可行解決嘅計算。Google就喺2019年話,佢哋53量子位Sycamore處理器完成一個超特別計算只需幾分鐘,而Google估計超級電腦要一萬年先做得切。(IBM就反駁話如果用最佳算法超級電腦都可以做得快啲,但呢個里程碑都意義重大。)
另一個相關概念係「量子優勢」(quantum advantage)。量子霸權係話任何一啲問題只要量子電腦做得好過傳統電腦就算,但量子優勢則係指量子電腦真係實際解決到有用問題,而且快過傳統電腦。換句話講,霸權只係概念驗證,優勢就係量子運算開始做到現實世界中重要事——例如物料科學模擬或者處理傳統電腦頭痛嘅複雜優化問題。
今日大部分量子電腦其實都仲係試驗階段。部機嘈吵又容易出錯,即係qubits好容易失去佢地纖細嘅量子狀態(叫做去相干)。而且qubit數量都仲算好少。例如IBM喺2022年發表最新「Osprey」處理器,已經有433請位(創紀錄);不過有專家估計,要破解現代加密制(例如比特幣),可能需要成百萬個優質量子位(下文再詳細講)。下圖係IBM Osprey量子處理器嘅電腦渲染圖 —— 重大突破,但距離威脅比特幣尚有一段距離。
連IBM負責量子硬件嘅高層都話,要實現「真正有用」嘅量子電腦,就要新架構,多顆晶片組合大型模組化系統。
呢個3D渲染圖係IBM 2022年推出433量子位「Osprey」量子處理器。類似處理器推高咗qubit數量,但專家話要攻破比特幣等加密貨幣用嘅密碼學,最少都要百萬級帶糾錯嘅量子位。(圖片來源:IBM/Connie Zhou,經路透社)
所以,雖然量子計算進步得好快,但唔係魔法。我哋仲未去到台上有部量子手提可以分分鐘破解所有密碼。至今為止所謂「量子霸權」示範,包括Google同中國研究團隊,只係做作性強、真實世界應用有限。「量子優勢」當目標,連最樂觀預測都話要數年後先見到。
短期內量子電腦仍主要係實驗室或雲端原型,解決嘅多數都係專門技術問題。不過形勢好清楚:能力一直提升,未來當佢解決到傳統電腦解決唔到嘅實用問題時,對好多行業(包括加密貨幣)都會有地震式影響。
點解比特幣加密未必永遠安全
比特幣成日俾人講到「冇得駭」,到目前為止主力密碼學的確做到。核心安全機制就係橢圓曲線數字簽名算法(ECDSA),呢種加密技術自1980年代起就用開,可以證明擁有比特幣資產。運作原理係:你有個私密號碼叫私人密鑰,由佢可以計算出一個公開密鑰,過程係同一組固定嘅橢圓曲線數學運算。
公開密鑰可以公開俾任何人——佢會雜湊組成你嘅比特幣地址——但私人密鑰只有你自己知道。如果你要用比特幣消費,就要用私人密鑰簽名;網絡用公開密鑰核實簽名來確認交易。最關鍵係,這條數學「只出不回」:用公開密鑰揾返私人密鑰,對傳統電腦嚟講幾乎唔可能。正如比特幣研究人員Nic Carter所講,比特幣安全性全賴一條「單向數學」:一邊易做,一邊傳統電腦基本唔可能倒算。現實係,試圖用普通電腦暴力破解256位私人密鑰,計算要用上億萬年——等於冇可能。
量子計算就可能打破這個不對等。1994年,數學家Peter Shor發現一個量子算法(Shor算法),可以有效解決ECDSA背後種數學問題。具體而言,Shor算法可極速做質因數分解同解離散對數,這啲都係現有傳統方法慢得多。ECDSA用嘅橢圓曲線離散對數正正屬於這類問題。簡單嚟講,只要有足夠先進嘅量子電腦跑Shor算法,就可以用公開密鑰搵返比特幣嘅私人密鑰,等於根本破解最核心防線。
攻擊者只要攞到目標嘅公開密鑰——而用戶一旦交易,公開密鑰通常會露喺區塊鏈上——未來量子攻擊者就能用來推算出私人密鑰,隨時用掉嗰個錢包內嘅比特幣。「不可破解」頓時變得脆弱。網絡安全公司Naoris Protocol行政總裁David Carvalho話,如果真係發生,表面睇錢包似乎冇異常:「一切表面都正常……你甚至唔會知」賊佬用量子電腦偷咗錢,因為對方完全可以產生正確簽名,好似錢包真正主人操作一樣。
受威脅其實唔止簽名算法。比特幣喺挖礦同產生地址時都用到密碼哈希函數,最常見係SHA–256。雖然哈希函數唔係直接受量子算法威脅(不像公開密鑰加密法咁危險),但都唔完全安全。量子電腦可以用Grover算法,加快搜索哈希碰撞或特定原像。Grover算法可以將暴力破解速度提升至原來嘅平方根速度。
以比特幣挖礦為例(基本就是暴力試算)…… race to find a SHA–256 hash below a certain target),利用 Grover 算法的量子電腦理論上能夠比傳統電腦快得多地挖礦。幸好,Grover 算法的優勢並不像 Shor 算法那麼致命。它實際上只會令哈希算法的強度減半:SHA–256 原本有 256 位元的輸出,在量子攻擊下安全程度大約下跌到 128 位元。128 位元的加密強度其實仍然非常高——作個對比,目前 128 位元的 AES 加密依然被認為達到軍事級別。
但如果量子硬件足夠強大,即使只是平方級的提速,也可能令裝有量子電腦的攻擊者在 Bitcoin 挖礦中獲得壓倒性優勢,甚至導致 51% 攻擊或者其他破壞。相比破解簽名這個威脅(因為挖礦難度等參數可以調整)來說,它暫時不是最迫切的風險,但始終構成憂慮的一部份。
總括而言,Bitcoin 所用的加密技術是在只有傳統電腦年代設計,設計人員預設有些數學難題實際上不可解(例如單靠公開密鑰不可能推出私密鑰)。量子計算徹底推翻這個假設。只要有夠多 qubit 及合適算法,以前被認為不可能的事全都有可能發生。正如密碼學家 Ethan Heilman 所講:「Bitcoin 需要保障用戶的資產跨世代安全」,即是要能抵抗不止是今日的電腦,連明日的科技都頂得住。
現實很殘酷:保護著 Bitcoin 及好多其他加密貨幣的加密技術,在量子發展下面「未必永久安全」。這也是為什麼過去純屬理論的量子威脅,近年隨量子實驗室逐步迫近破解 ECDSA 及其他舊式加密的能力而變得愈來愈受重視。
The “Quantum Attack” Scenario: What If It Already Happened?
One chilling aspect of a quantum attack on Bitcoin is that it could unfold in silence, without obvious signs of intrusion. If a quantum computer powerful enough to crack Bitcoin’s keys came online today, it’s possible coins could start moving from wallets and nobody would immediately realize those transactions were fraudulent. “If a quantum computer capable of breaking modern encryption were to come online today, Bitcoin would likely be under attack – and no one would know,” Carvalho warned in an interview.
原因是,量子竊賊根本毋須入侵網絡或偽造代幣;他們只要破解特定帳戶的私密鑰,然後用來簽發合法交易即可。區塊鏈上看來,這些交易和任何正常用戶簽名的交易無異。
想像下你一覺醒來,見到一個十幾年都無郁過的早期 Bitcoin 地址突然將所有 BTC 轉走去一個未知錢包。鏈上分析師或者只會懷疑是否某個失蹤多年的持有人回歸,但在量子盜竊場景下,實際上可能是攻擊者計算出該地址的私密鑰並洗劫一空。區塊鏈會依舊穩穩運行,區塊正常開採、交易正常確認,而某些幣的擁有權則暗中轉移。如 Carvalho 所講:「你只會見到啲幣好似持有人決定使用咁轉走,」帳本上絕對無任何失敗簽名或明顯異常紅旗。
哪些幣最危險?專家指最早期、最長期沒動過的錢包是頭號目標。後量子創業公司 Quranium 創辦人 Kapil Dhiman 指出,Bitcoin 最早期的地址(包括中本聰傳說中的積蓄)以現今標準計加密實踐不夠安全。
比如好多早期比特幣都存在 P2PK 地址——公開密鑰是直接寫在鏈上的(不像現代 P2PKH,直到消費時才揭示)。「中本聰啲幣簡直係『坐定粒六』,」Dhiman 告訴 Cointelegraph,指約有 100 萬 BTC 被認為由創辦人開採過。如果這些塵封多年的幣突然轉走,信心將瞬間破滅——大家可能以為係中本聰回歸,還是量子駭客出擊,無論邊個情景都會極大破壞市場穩定。
撇開中本聰,任何重複用過地址或將公開密鑰暴露的錢包同樣處於高危。德勤一份研究估算截至 2022 年,流通中的 Bitcoin 大約有 25% 可被視為對簽名算法量子攻擊「不安全」。這包括舊式地址,以及曾經多次用過的地址(因而公開過密鑰)。相反,約 75% 幣仍屬「安全」地址(至少在地址未曾動用之前)。但長遠而言,只要一做交易,「安全」地址都一樣會變成不安全,因為花費時通常會公開公開密鑰。
如果量子竊賊開始悄悄偷竊,短期內會點?有機會出現恐慌。一旦用戶發現高價值錢包被清空就會爭相拋售,引發價格暴跌。但追查責任會很困難:到底係量子駭客,定係傳統方法洩漏密鑰?按設計,量子攻擊的證據可以藏在白紙黑字的區塊鏈之中。「當你終於懷疑出現量子電腦,其實可能已經暗中控制咗條鏈幾個月,」Carvalho 警告,意即等到公眾開始懷疑,好多財富早被不知不覺間竊走。
佢用一個發人深省的例子比喻:二戰盟軍破解德軍 Enigma 密碼機,但為免暴露突破,寧願有時候假裝唔識,讓部分攻擊成功。今日某國一旦擁有量子電腦,也很可能傾向暗中盡量榨取 Bitcoin 加密優勢,而不是公然宣佈實力。
要強調的是,暫時這一切仍屬理論推測。現時無任何公開證據顯示有人已擁有足以達到呢種能力的量子電腦——「科學界、研究界和軍方的一致共識都認為未見其事發生,」Carvalho 指出。但佢亦加多句:「這亦不是世界首例在無公眾知情下被破解的頂級加密。」除非有人公開證明,否則大家只能假定 Bitcoin 尚屬安全。
即使如此,單是這種無法察覺的量子攻擊可能性已經值得大家極度警覺。正因如此,有安全專家把量子風險視為迫切的工程問題,而不是科幻假想;有研究員甚至直言:「要有預案。」如果等到幣開始詭異消失才來反應,大概已太遲,難以挽回損失。
Timeline: How Close Are We to a Quantum Threat Reality?
最值錢的問題:量子電腦幾時先會強到真正威脅到 Bitcoin 的加密技術?專家意見分歧——有人估「可能十幾二十年」,有人講「未必我們有生之年見到」,亦有人認為「可能比想像早」。科學主流一致傾向認為威脅最少超過 10 年後先出現,但都帶有變數及極少數反對聲音。
國際安全機構和標準組織的時間表有參考價值。美國國家標準及技術研究院(NIST)一直領導制定後量子加密標準,建議在 2035 年前過渡到耐量子算法作預防。佢哋唔係話到 2035 就會有足以破解加密的大型量子電腦,而係考慮所謂「現在收割,遲啲解密」風險:對手可能今日已記錄加密資料(或者摷區塊鏈公開密鑰),預計將來有量子機就會解密。
NIST 的時間線暗示,到 2030 年代,量子電腦可能已經足以威脅到某部分密碼學,以致長期資料加密安全受威脅。不過業界有人指出,比特幣未必同一般加密通訊哋咁急需防衛。Ledger 技術總監 Charles Guillemet 指,NIST 2035 指引其實針對「前向安全性」(即今日保密資料將來都唔會被解密),而 Bitcoin 交易本身並不保密。他認為 Bitcoin 最大風險在於有人能即場偷私密鑰(而不是回頭破解舊密文),即還有少許緩衝期。
至於量子硬件進展:IBM 的路線圖預計到 2033 年有幾千個 qubit 的處理器,距離破解 Bitcoin 256 位元密鑰所需的數百萬 qubit 仍差好遠。現時最大公開量子晶片是 IBM 的 433 qubit“ Osprey”(2022年),目標在 2023–2024 年推出突破 1,000 qubit 的“ Condor”,繼續蒸蒸日上。Google 方面預計十年內(約 2029 年)會造到具容錯機制、持續可用的量子電腦——即可靠運行量子演算法的機器。
這些進度很進取,但沒保證必定如期成功。值得注意的是,即使有幾千 qubit 都唔夠破解 Bitcoin;這些 qubit 質素亦要非常高(極低錯誤率),而演算法亦需高度最優化。有學術研究估算,要在 24 小時內用 Shor 算法破解一條 Bitcoin 私密鑰,量子電腦需要大約 1300 萬個 qubit。現時 433 甚至 1,000 qubit 只係「滄海一粟」。
業界專家通常會幫大家降溫。2025 年初,Nvidia 行政總裁黃仁勳——其GPUs 係用咗喺一啲量子控制系統入面——所謂「非常有用嘅量子電腦」大概仲有二十年先到。「你話十五年,咁就算早咗啲;你話三十年,可能就遲咗啲。不如揀二十年啦。」黃進一步解釋,暗示前路仲好長。同樣,區塊鏈加密貨幣先驅 Adam Back 就一向無理會啲聲稱話比特幣可以喺 2028 年之前俾量子電腦破解嘅講法,佢直言:「冇可能啦」,仲諗過要對賭。Back 估計,可能要到廿年後先真係需要擔心。
另一位著名比特幣人士 Samson Mow 就話量子計算係「一個真實嘅風險,不過時間表可能仲有十年咁遠」,並補充話,佢自己認為「就算真係出現威脅,其他嘢都會先 fail,好過比特幣 fail」。這啲睇法都反映咗比特幣開發社群一個共通立場:保持審慎監察,而唔係即刻恐慌。
不過,亦有啲人好大聲呼籲要加快步伐。好似 Solana 嘅 Anatoly Yakovenko,據講,佢覺得到 2030 年有突破嘅機會係一半一半,並話而家啲相關科技(例如 AI)發展得咁快,形容量子嘅突破可能會比預期早,等我哋「大跌眼鏡」。去到 2023 年年中,曾有 Google Quantum AI 路線圖洩漏,暗示未來幾年 qubit 數量會大幅上升,引發咗市場揣測。
而講到國家安全,就唔可以排除有啲技術突破係秘密進行——政府實驗室未必會公開所有成果,特別係對情報有價值嘅,所以加密學家 Michele Mosca 就提出咗「Q–day」——即係量子電腦可以破解現有加密嘅嗰日。佢同其他專家都警告,Q–day 隨時可以突如其來、快過預期,搵啲以為仲有大把時間嘅人措手不及。
總括而言,去到 2025 年,大部分估算都話量子威脅對現行加密標準喺 2030 年代或之後先至會成真。例如 Bernstein 分析師有份報告,都仍然認為「呢個威脅仲有幾十年先到。」但其實只要有一次突破,大家共識都可以即刻改變。2022 年尾就試過有中國研究人員聲稱發明咗一種新嘅因數分解方法——如果真係可以擴展,可能會大大降低量子融合攻擊 RSA 私鑰嘅門檻。
呢個說法後來引嚟健康嘅懷疑,多數都唔認為會構成真正攻擊,但都發咗個警號:技術突破有可能從不同方向出現,而我哋往往會低估咗有咩做得到。正如理論計算機科學家 Scott Aaronson 所寫,謹慎嘅態度應該係「係,依家就要擔心,仲要有預案。」早做規劃就算量子解密能力提早到,都唔會令整個加密界全軍盡墨。
Post–Quantum Cryptography: 有咩應對方案?
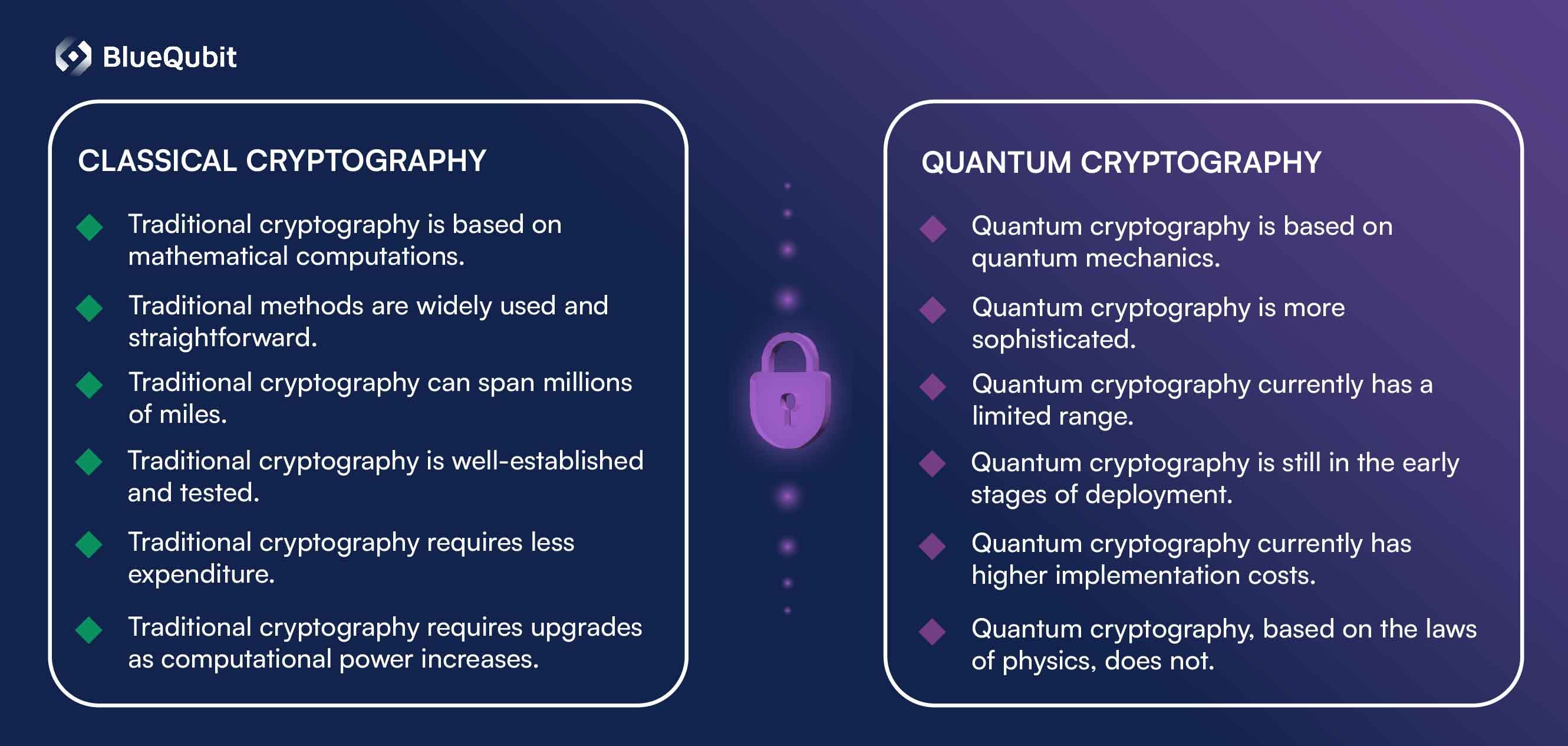
好消息係,加密界唔係坐喺度等 Q–day 嚟。有個叫後量子加密(PQC,Post-Quantum Cryptography)嘅研究範疇,一直都喺開發一啲可以頂住量子電腦攻擊嘅新算法。呢啲同「量子加密」唔同——量子加密通常係講用量子物理(好似量子密鑰分發);而 PQC 就係用經典計算機運行嘅演算法,但設計成量子對手都難以破解咁囉。
2016 年,美國 NIST 開咗個公開比賽,去揀最合適嘅 PQC 算法。經過幾輪評審,2022 年 Announce 咗第一批標準化後量子加密演算法,包括:
- CRYSTALS–Kyber:一種基於格(lattice–based)嘅密鑰封裝方案(用嚟加密資料或者建立共享密鑰)。
- CRYSTALS–Dilithium:一個基於格嘅數碼簽名方案。
- FALCON:又一個基於格嘅簽名(簽名細啲,不過實現複雜啲)。
- SPHINCS+:一種基於 Hash 嘅、無狀態(stateless)數碼簽名方案(無需追蹤用過嘅密鑰)。
去到 2024 年,NIST finalize 咗以上演算法嘅標準(Kyber 負責一般加密,Dilithium 同 FALCON 做簽名,SPHINCS+ 做備用簽名),並以 FIPS 203–205 發布。普通人理解,即係如果我哋將比特幣嘅 ECDSA 同 SHA-256 換咗做新嘅 PQC 演算法組合,就可以抵禦已知嘅量子攻擊啦。
舉例,現時用緊橢圓曲線簽名,可以換做基於格嘅 Dilithium,或者基於 Hash 嘅 SPHINCS+。呢啲演算法靠啲「目前認為量子機破解唔到」嘅數學難題(例如 lattice 問題難度大,或者 cryptographic hash function 嘅安全性),就算 Shor’s 或 Grover’s 方法都唔會短時間內破解到。
不過,真係要喺區塊鏈實行 PQC,又唔係話咁簡單。PQC 算法經常有 trade-off:例如私鑰/簽名會大咗,速度慢咗之類。以 Dilithium 做例子,佢嘅簽名大約幾 KB(對比 ECDSA 係 64 bytes),可能會令區塊鏈交易膨脹。SPHINCS+ 呢類 Hash-based 簽名就仲大同埋驗證慢啲,不過基礎安全係來自可靠嘅 Hash。雖然有啲缺點,轉型其實都做得到。都已經有加密項目由一開始就標榜抗量子。
例如 Quantum Resistant Ledger (QRL) 就係一條一出世就用後量子(Hash–based、類似 SPHINCS+)簽名(XMSS)嘅區塊鏈。QRL 揀 XMSS 就係為咗防未來量子攻擊,不過有條件:每個地址只能夠安全簽有限次,簽完就要換 key(屬於有狀態 Hash-based 簽名嘅限制)。另一個項目 QANplatform(雖然上面無提,不過行內都識),就話用 lattice–based 加密去保護佢啲智能合約平台。
Quranium(Kapil Dhiman 領導),就用咗 NIST 批准嘅無狀態 Hash-based 簽名方案去保護佢層一區塊鏈。至於 Naoris Protocol 嘅 David Carvalho(之前都有提),佢哋就搭建緊後量子基建,遞交到美國證監會(SEC)討論量子安全標準。呢啲小項目影響力未算大,但都係區塊鏈後量子實踐嘅試驗場。而且做到類似保險效果:如果大鏈轉得慢,量子破解真係嚟臨時,理論上可以將資產搬去 QRL 呢啲抗量子鏈保住(如果一切有秩序進行)。
主流區塊鏈都研究緊方案。例如 Ethereum 都討論過同 Prototype 過後量子加密。以太坊開發者探索過 lattice–based 簽名、甚至零知識證明(zk–SNARKs)嘅後量子變體。Ethereum Foundation 有文講點用 lattice–based BLS 簽名去 post–quantum。暫時都仲未正式用落生產環境——依家 Ethereum 用 ECDSA 同 BLS(做 validator 簽名)一樣有原理上被量子攻擊嘅風險。不過都鋪咗條路。
除咗數碼簽名,其實礦工運作/共識流程都可以諗下點抗量子。例如比特幣 proof–of–work,只要 Grover 算法真係成威脅,可以升級用更長嘅 hash(SHA–512 或更進階版本)去增強。有啲人甚至建議比特幣要喺量子機出現之前轉 PoS(proof–of–stake),話咁就唔需要靠 brute force 賽跑咁多(雖然 PoS 都有本身嘅假設同風險)。以上都係推測,畢竟比特幣社群對呢啲根本性改動態度都好保守。
另一條線就係直接用量子加密——例如量子密鑰分發(QKD),用量子物理份真假,兩邊產生共享密鑰,有人偷聽就一定 detect 到。QKD 唔適合去中心化鏈(無 point-to-point link),不過一些機構其實可以用喺區塊鏈系統入面,保障通訊渠道。
2022 年,摩根大通同東芝示範過一個用 QKD 加密、抵禦量子劫持嘅區塊鏈網絡,基本上層層疊加量子安全通訊係區塊鏈上面。呢種方法可能未來多啲應用喺私有賬本或者銀行之間。不過對於公有加密貨幣,主力方案始終係演算法升級去 PQC。
總結返而家嘅解決方案:幾年嚟 NIST 同業內不斷研究,有一批後量子算法經驗證,已經 ready /好快 ready deploy。有啲 crypto 先行者已經喺新平台試緊。有唔同提案(下文會講)建議主流鏈點樣逐步遷移。技術層面,要保護加密資產係做得切嘅,最大挑戰反而係社會同協調——點先可以齊心同時幫百萬用家同關鍵基建轉型過去。正如一位網安公司 CEO Chris Erven 所講:「宜家係時候將量子安全技術納入全球網安核心策略」,要主動做埋去——唔好臨急抱佛腳!
加密貨幣同傳統金融比較進度
提到準備對抗量子威脅,傳統金融同政府世界其實可能行得快過 crypto 界。大銀行、大企業、政府機構最大優勢就係集中管...security upgrades top–down. Cryptocurrencies, by contrast, are decentralized by design, which makes coordinated transitions more complicated.
由上而下進行保安升級。相反,加密貨幣本身是去中心化設計,協調轉換變得更加複雜。
Take the banking sector: JPMorgan Chase has been notably proactive. In addition to the quantum key distribution experiment mentioned earlier, JPMorgan has a “Future Lab” for quantum technologies. Marco Pistoia, who leads that lab, said the bank is preparing “for the introduction of production–quality quantum computers” precisely because they could “change the security landscape of technologies like blockchain and cryptocurrency in the foreseeable future”. JPMorgan isn’t waiting for an emergency; they’re testing defenses now. Similarly, the global banking network SWIFT has launched training programs and workshops on post–quantum security for its member institutions.
以銀行業為例:摩根大通(JPMorgan Chase)一向極為主動。除咗上面提到嘅量子密鑰分配實驗,JPMorgan 仲有個專為量子技術設立嘅「未來實驗室」。帶領嗰個實驗室嘅 Marco Pistoia 表示,銀行正準備「迎接可以實際投產嘅量子電腦嘅出現」,正因為佢哋會「喺可見未來改變區塊鏈同加密貨幣等技術嘅安全形勢」。JPMorgan 並無等到緊急先行動;佢哋而家已經開始測試防禦。同樣,全球銀行網絡 SWIFT 已經為旗下機構推出有關後量子安全嘅培訓計劃及工作坊。
Companies like IBM and Microsoft are already offering quantum–safe encryption options in their cloud products, so that companies can start encrypting data with algorithms like Kyber or Dilithium ahead of time. The U.S. government passed the Quantum Computing Cybersecurity Preparedness Act (in late 2022), which requires federal agencies to begin planning to migrate their systems to post–quantum cryptography. In 2015, even the NSA (which historically helped curate US encryption standards) announced plans to transition to quantum–resistant algorithms – a strong signal to industry and academia to get moving.
IBM、Microsoft 呢類公司已經喺佢哋嘅雲端產品提供量子安全加密選項,等企業可以預早用 Kyber 或 Dilithium 等演算法加密數據。美國政府亦喺 2022 年尾通過咗《量子計算機網絡安全準備法》,要求聯邦機構開始規劃點樣將系統遷移至後量子加密。早喺 2015 年,連一向負責制訂美國加密標準嘅 NSA 都宣布咗計劃轉用抗量子解算法——向業界同學術界發出咗強烈訊號,要加快行動。
Now compare that to the state of most cryptocurrency networks: Bitcoin, Ethereum, and the majority of altcoins still use RSA, ECDSA, or EdDSA signatures and standard hashing (SHA–2, SHA–3, etc.). There has been no urgent migration yet. Part of the reason is that, as we discussed, many in the community believe the threat is not imminent. Another part is the challenge of consensus: to change Bitcoin’s signature algorithm, for example, literally every participant in the network needs to agree (or at least a supermajority, if done via soft fork).
對比返加密貨幣網絡現狀:比特幣、以太坊同大部份山寨幣依然用緊 RSA、ECDSA、EdDSA 呢啲簽名同標準雜湊法(SHA–2、SHA–3 等)。暫時未見有急切性嘅轉移。部分原因係,正如之前所講,好多圈內人唔認為威脅迫在眉睫。另一個原因,就係共識難題:例如要改比特幣嘅簽名算法,基本上全網所有參與者都要同意(或者話,如果係 soft fork,起碼要絕大多數通過)。
That’s a slow process involving proposals, coding, testing, and convincing the global user base. “Traditional finance is actually ahead,” as Naoris’ Carvalho observed. “They have central control, budgets and a single authority that can push upgrades. Crypto doesn’t have that. Everything takes a consensus.” In other words, Jamie Dimon can tell JPMorgan’s security team “we’re switching all internal communications to post–quantum encryption next year” and it’ll likely happen.
呢個流程慢到不得了,要經歷提案、編碼、測試、同說服全球使用者。「傳統金融其實跑得更前,」Naoris 嘅 Carvalho 指出:「人哋有中央權力、有預算、有一個權威可以推進升級。加密貨幣就唔同,樣樣都要大家有共識先得。」換句話講,Jamie Dimon 可以一聲令下,話「我哋明年全部內部通訊都轉用後量子加密」,實行機會好高。
There’s no analogous figure in Bitcoin who can unilaterally decree a crypto upgrade – by design, it’s nobody’s call alone. We’re seeing some movement in the crypto space though. The fact that Bitcoin developers are drafting quantum–mitigation proposals now (in 2023–2025) shows the gap is understood. And some crypto companies are getting involved in the broader PQC effort. For instance, blockchain security firms and academic collaborations are exploring crypto–agility – designing protocols that can swap out cryptographic primitives more easily in the future. The ideal scenario is to make blockchain networks as nimble as web browsers, which can (in theory) roll out new cryptography via updates when needed. But getting millions of decentralized nodes to update is a bigger undertaking than updating, say, Google Chrome or Firefox on user devices.
比特幣冇一個人可以一言堂咁宣布要搞加密升級——設計上就係冇人可以話事。不過加密界都有啲動作。事實上,比特幣開發者依家(2023–2025)正撰寫相關量子威脅緩解建議,說明大家理解到存在差距。亦有啲加密公司積極參與更大範圍嘅 PQC(後量子加密)大計。例如,區塊鏈安全公司同學術界正研究「加密敏捷」,即設計協議方便將來可以輕鬆更換加密基礎工具。理想情況下,區塊鏈網絡可以快得好似瀏覽器一樣,需要時可以用更新方式推出新加密技術。但要全世界咁多分散節點一齊更新,比喺用戶電腦上更新 Google Chrome 或 Firefox 嚴重得多。
Another point of contrast is the risk surface. Traditional finance relies heavily on encryption for secure communication (TLS for banking websites, VPNs, secure messaging, etc.), all of which could be undone by a quantum attacker. So banks face not only the threat of cryptocurrency theft but also potentially the exposure of sensitive customer data and financial transactions if encryption breaks. This gives them a broad incentive to upgrade everything encryption–related.
另一個對比位就係風險層面。傳統金融極度依賴加密通訊(例如銀行網站用 TLS、VPN、安全訊息等等),一旦有量子攻擊者,全部都可以被破解。所以銀行唔單止要擔心加密貨幣被偷,仲有可能因加密技術失效,導致敏感客戶資料同金融交易被曝光。咁就俾咗銀行一個強大動力,將所有加密相關嘢齊齊升級。
Cryptocurrencies have a narrower but more acute risk: the integrity of the currency itself. A quantum attack on crypto doesn’t reveal confidential information (since blockchains are public), but it could undermine ownership and trust in the system. In some sense, the crypto risk is “all or nothing” – either your coin’s algorithm gets broken and chaos ensues, or it doesn’t. Banks meanwhile might survive some breaches but face massive privacy or financial losses if they drag their feet on PQC.
加密貨幣則係風險範圍窄啲但嚴重啲:就係貨幣本身嘅完整性。量子攻擊唔會披露機密(因為區塊鏈本來就公開),但會破壞所有權同對系統嘅信任。可以話,加密貨幣嘅風險係「一係冇事,一係攬炒」——只要加密算法畀人破解,個體系即時大亂;否則就冇事。銀行就算俾人爆破一部分,都可能捱得住,但如果拖延轉去 PQC,就有機會蝕身家或者洩露大量私隱。
Interestingly, some collaborations are emerging between tradfi and crypto on this issue. JPMorgan’s quantum–safe blockchain network could be seen as a private blockchain use case, but the tech could potentially inform public chains too. IBM, being a major player in both enterprise blockchain and quantum computing, might eventually help bridge solutions into the open–source blockchain world. And governments might impose standards – for example, one could imagine a future regulation that says any cryptocurrency used by banks or traded on regulated exchanges must be quantum–resistant by a certain date. That would light a fire under the decentralized projects to adapt or face delisting.
有趣嘅係,傳統金融同加密界喺呢個問題上開始有啲合作。摩根大通搞緊嘅量子安全區塊鏈雖然係私人鏈,但啲技術日後可能都幫到公鏈。IBM 做企業區塊鏈同量子計算都係大玩家,或者將來會將解決方案引入開源區塊鏈。而政府都可能會出標準——試想像下,將來如果規定所有銀行用或者喺受規範交易所交易嘅加密貨幣,到某日之前都要做到量子防護,咁啲去中心化項目就必然迫住要配合,唔然可能會被下架。
In summary, the traditional finance world has started the post–quantum transition in earnest, leveraging their centralized structure to do so. The crypto world lags behind not due to ignorance but due to the inherent difficulty of making protocol changes in a decentralized environment and a perhaps justified sense that the danger isn’t right at the doorstep yet. The challenge ahead is accelerating crypto’s migration pace without undermining the qualities (decentralization, stability) that make it valuable. It’s a delicate balance of not crying wolf too early versus not sticking one’s head in the sand. The next section will delve into how Bitcoin might approach this in practice, which illustrates just how complex that governance process can be.
總結嚟講,傳統金融界已經認真展開後量子過渡,而且利用咗佢哋中心化架構優勢去推進。加密世界唔係因為無知而落後,而係本身喺去中心化環境下要改協議特別難,再加上佢哋認為危機未到眼前。之後最大挑戰,就係點樣加快加密貨幣世界嘅遷移速度,而又唔會破壞其本有價值(去中心化、穩定性)。要拿捏唔好太早大叫狼來了,又唔好當冇事發生。下一節會深入講下比特幣如果真要遷移,實際會點做,同時都反映治理過程有幾複雜。
What If Bitcoin Migrates? The Governance Challenge
Let’s say the Bitcoin community collectively decides, “Yes, we need to upgrade our cryptography to be quantum–safe.” How would that actually happen? This is where the governance challenge kicks in. Upgrading Bitcoin is often compared to repairing an airplane mid–flight – any change must be carefully designed not to break the system as it runs. For a quantum–resistant Bitcoin, developers have proposed a few routes, each with pros and cons.
假設比特幣社群一致認為:「係,應該升級加密技術,確保抗量子攻擊。」咁實際會點搞?治理難題就係響呢度出現。升級比特幣成日俾人比喻為「飛緊嘅飛機入面維修」——系統運行期間,任何更改都要設計到極之小心,唔可以搞到壞系統。針對抗量子比特幣,開發者有幾個路線提議,各有利弊。
One key proposal making rounds is known as BIP–360, also nicknamed “Bitcoin Post–Quantum” or “QuBit” (not to be confused with qubit, the quantum bit). BIP–360 is a draft Bitcoin Improvement Proposal by a pseudonymous author “Hunter Beast” that sketches a multi–stage plan to introduce quantum–resistant addresses and signatures to Bitcoin. The idea is to do it gradually to avoid chaos. Here’s a simplified rundown of the plan:
其中一個主要方案就叫 BIP–360,俗稱「Bitcoin Post–Quantum」或者「QuBit」(唔好同量子比特 qubit 混淆)。BIP–360 係一個化名為 Hunter Beast 嘅作者寫嘅 Bitcoin Improvement Proposal 草案,設計咗一個多階段計劃,點樣逐步引入抗量子地址同簽名去比特幣。重點就係分階段嚟,避免亂晒大龍。簡單總結如下:
Stage 1: Introduce a new address format, called P2QRH (Pay–to–Quantum–Resistant–Hash), that can support various post–quantum signature algorithms. Users could start creating new addresses of this type and sending Bitcoin to them. These addresses would be backwards–compatible (they’d look like any other address to old nodes, likely via some versioning), so this can be done as a soft fork.
第一步:推出一種新地址格式,叫 P2QRH(Pay–to–Quantum–Resistant–Hash),支援多種後量子簽名算法。用戶可以開始建立呢類新地址,再將比特幣轉去。呢啲地址會兼容舊系統(舊節點睇落去同舊地址差唔多,可能靠版本辨認),所以可以用軟分叉方式實施。
Stage 2: Once P2QRH addresses exist, give people an incentive to use them. QuBit proposes a block weight discount (16x cheaper in terms of fees) for transactions from quantum–resistant addresses. This is similar to how SegWit’s rollout gave discounts to encourage adoption. Cheaper fees would nudge wallets and users to migrate funds to the new address type over time.
第二步:有咗 P2QRH 地址之後,要俾誘因大家用。QuBit 建議用抗量子地址進行交易,可以享有區塊容量優惠(手續費平 16 倍)。呢個策略同當年 SegWit rollout 時俾轉用優惠有啲似。手續費低咗,自然會慢慢催促用戶同錢包慢慢將資金遷移去新地址類型。
Stage 3: Develop a Taproot–compatible version of these addresses, and eventually make a soft fork that begins to require quantum–resistant signatures for new transactions. At this point, perhaps after many years of voluntary adoption, the community might agree to “sunset” the old ECDSA–based addresses.
第三步:研發到同 Taproot 兼容版新地址,然後實行軟分叉——開始要求新交易必須用抗量子簽名。做到呢一步,可能已經過咗好多年自願逐步採用,社群到時或會同意「收山」舊 ECDSA 地址。
Stage 4: In the far future, once it’s confirmed that quantum threat is imminent, a final soft fork could disable old signature types entirely, making Bitcoin fully post–quantum for all transactions going forward.
第四步:等到將來量子威脅真係近在眉睫,最尾可以再做一個軟分叉,徹底禁用所有舊類型簽名,令比特幣所有交易都全面進入後量子時代。
This phased approach is meant to tackle governance pragmatically: don’t force everyone to switch on a dime (which would be a hard fork and contentious), but rather introduce the new system, encourage its use, and slowly make it the default. By using soft forks, backward compatibility is maintained – old nodes would see a P2QRH transaction as anyone–can–spend (if not aware of the new rules) but thanks to miner enforcement, it would still be secure. It’s complex engineering, but Bitcoin has navigated tricky upgrades like SegWit in the past.
呢種分階段方式,就係想以務實方式疏理治理問題:唔會逼人即刻轉(咁只會變成激烈又有爭議性嘅硬分叉),反而慢慢推新系統、鼓勵採用,直到最後變做預設。咁做可以保留軟分叉向後兼容性——舊節點見到 P2QRH 交易會當成 anyone-can-spend(如果佢唔知新規則),但有礦工商定都可以保障安全。雖然技術含量高,但比特幣過往應付過類似(如 SegWit)升級挑戰。
There are some trade–offs and open questions. Quantum–resistant signatures are big, so if a lot of people start using them, it could effectively reduce how many transactions fit in a block (hence discussions of a block size increase have floated around in conjunction). QuBit’s current iteration suggests that using PQ signatures might effectively lower throughput somewhat, but it considers that an acceptable price for security. There’s also the matter of which quantum–safe algorithms to choose.
當然,亦有啲 trade-off 同未解決問題。例如抗量子簽名通常體積大咗好多,如果一旦多人用,可能每個區塊可以承載嘅交易數目會少咗(所以坊間同步都有人討論要唔要加大 block size)。QuBit 現有計劃書認為,如果 PQ 簽名令吞吐量跌一啲都係安全換來嘅可接受代價。仲有——到底選邊隻抗量子算法?
QuBit smartly doesn’t lock in one algorithm; it supports a few (like SPHINCS+–256F and FALCON–1024) and lets users pick. This hedges against any single new algorithm later being found flawed – a wise move given PQC is relatively new and not battle–tested like RSA/ECC. Still, more exotic options like lattice signatures could introduce their own uncertainties (e.g., if a breakthrough math attack on lattices happened, that could be an issue; it’s not likely, but it’s the kind of thing cryptographers consider).
QuBit 明智地冇死咬一隻算法,而係支援幾種(例如 SPHINCS+–256F、FALCON–1024),俾用戶自由揀。咁做好處係萬一其中一隻新算法之後出事,都可以分散風險——特別 PQC 相對新,冇 RSA/ECC 咁經過實戰驗證。不過,有啲更特別嘅選項(例如 lattice 圖像簽名)都可能帶來新問題(例如果真有數學層面重大突破攻擊 lattice,咁就大鑊啦——雖然機會低,但密碼學家都會考慮呢啲)。
An alternative strategy is more brute–force: a hard fork to mandate post–quantum crypto across the board. This would be simpler in execution (just change the rules at block X so that only PQ signatures are valid going forward), but politically and practically it’s far harder. Hard forks can split the chain if not everyone agrees –
另一種策略就係簡單粗暴 D:來一次硬分叉,強制全網用抗量子加密,淨係新規則生效(例如規定到某個區塊高度後,只接受 PQ 簽名)。執行上好簡單,但實際推動同政治層面都極之困難,因為硬分叉一旦出現分歧好易劈出兩條鏈——think of Bitcoin Cash splitting off in 2017 over a disagreement.
諗下2017年嘅Bitcoin Cash因為意見不合而分叉。
If a significant minority of users or miners refuses a quantum–hard–fork (perhaps because they disagree on timing or algorithm choice), you could end up with two competing Bitcoins, which would be a nightmare for value and trust. So, most see a hard fork for quantum as a last resort, perhaps only if an emergency dictates it and there’s near–unanimous consent out of sheer necessity.
如果有一大部分用戶或礦工拒絕量子硬分叉(可能因為唔同意時間或者演算法選擇),最終可能會出現兩個互相競爭嘅比特幣,對於價值同信心都係場噩夢。所以,大多數人都認為量子硬分叉係最後一步,得喺非常緊急又幾乎全體同意嘅情況下先會用。
We should also consider the user aspect: ordinary Bitcoin holders would need to move their coins to new addresses at some point to be safe. As long as they have their private keys, they can always spend from an old address into a new one. But some coins are lost or held by people who aren’t paying attention. Those coins might remain forever in vulnerable addresses.
都要諗下用戶層面:普通持有比特幣嘅人,到時都要將啲錢移去新地址先至安全。只要佢哋有私鑰,隨時可以由舊地址轉賬去新地址。但係有啲幣已經唔見咗,或者揸住啲幣嗰啲人根本冇留意,咁啲幣就可能永遠留喺有漏洞嘅地址,變得危險。
One proposal (floated academically) is that if quantum computing arrives and some coins haven’t moved, there could be a “vaulting” or recovery process to protect them (perhaps miners temporarily freeze obvious quantum–theft attempts or something). However, that gets into very contentious territory of potentially violating Bitcoin’s fungibility or allowing special cases, which the community would be loath to do. Realistically, if someone doesn’t upgrade their coins after years of warning and then they get stolen by a quantum attacker, it would just be part of the fallout.
有一個學術上提出嘅方案係:如果量子電腦面世,有啲幣仲未搬,可能要有個「保險庫」或者回收機制去保護啲幣(例如礦工暫時凍結好明顯係量子盜竊企圖嘅交易等)。但係,咁樣就好有爭議,因為可能會破壞比特幣嘅可替代性,又或者容許特殊例外,社群一般都唔接受。現實啲講,如果有人經過咁多年警告都唔upgrade,真係比量子攻擊者偷走咗,都只可以當係後果之一。
It’s worth mentioning that Ethereum and other smart contract platforms face a similar governance challenge. Ethereum’s culture is more open to upgrades (they hard–fork regularly for improvements), so it might execute a quantum–safe transition faster if needed. There’s even the possibility of using Ethereum’s programmability to allow both old and new signature types to coexist until a cutoff.
值得一提,Ethereum同其他智能合約平台都面對住類似嘅治理挑戰。Ethereum文化本身對升級比較開放(經常用硬分叉改進系統),如果要做量子安全轉型,可能動作會快啲。甚至可以用Ethereum本身有嘅編程能力,做一個新舊簽名類型可以同時存在直到截止日嘅過渡方案。
Some altcoins like Nano, Stellar, etc., use different signature schemes (like ed25519) which are equally vulnerable to quantum, so they’d need upgrades too. It’s a broad ecosystem issue. Coordination across chains isn’t strictly necessary (each network can handle itself), but imagine the scenario where one major coin goes PQ and others haven’t yet – there could be market shifts and arbitrage around perceived security.
有啲altcoin,例如Nano、Stellar等,雖然用唔同嘅簽名算法(例如ed25519),都一樣會畀量子電腦破解,所以都要升級。呢個係整個生態圈嘅共同問題。各條鏈未必要一齊做(每條鏈可以自己搞掂自己事),但試想像有某條主流幣率先變成抗量子,而其他都未做——市場信心會轉移,仲可能出現圍繞安全感嘅套利機會。
In short, migrating a cryptocurrency to quantum–safe crypto is as much a social process as a technical one. It requires developers to write the code, yes, but then also miners to adopt it, businesses to update their systems, wallet providers to create user–friendly tools (so people can convert their funds to new addresses easily), and exchanges to recognize the new address formats. It’s a multi–year effort. The governance challenge is keeping everyone aligned and moving roughly in step rather than fracturing.
簡單講,將加密貨幣升級做抗量子,技術要搞,但係社群協調仲更加關鍵。要開發者寫好code,礦工肯用,商業機構要跟住update,錢包公司要做好用啲嘅工具(方便大家搬錢去新地址),交易所都要識新地址格式。成個過程要幾年,最大挑戰係唔好因為分歧而散咗,而要大家一齊步伐行前。
So far, Bitcoin’s community has shown it can rise to challenges when truly needed (e.g., the response to bugs or scalability issues), though not without drama. The looming quantum threat might actually serve as a unifying issue – nobody in crypto wants to see the coins broken. As long as the timeline is understood, one would hope even usually feuding factions of the community would come together to defend their collective interest: the integrity of the network.
迄今,Bitcoin社群已經證明當遇到真正危機,可以一齊齊心應對(例如bug或者擴展問題),雖然唔少爭拗。今次量子威脅反而有機會成為凝聚大家嘅議題——冇人想見到加密幣玩完。只要大家睇清楚大局,就算平時成日鬥爭嘅派系,都應該會為咗守住網絡完整性而暫時和解。
Winners, Losers, and Economic Consequences
贏家、輸家同經濟後果
What would the crypto landscape look like if quantum computing reached the point of breaking contemporary encryption? It’s a scenario that could produce some clear winners and losers, at least in the short term, and broadly shake economic confidence in digital assets.
如果量子電腦可以破解現有加密技術,加密貨幣世界會變成點?最少短期內一定有人贏有人輸,而且對數碼資產信心會有巨大衝擊。
First, let’s consider the worst–case event: a sudden quantum attack becomes feasible and is unleashed on an unprepared network like Bitcoin. The immediate loser would be trust. Confidence in the security of cryptocurrency could evaporate overnight. Prices of major coins would likely plummet as holders scramble to sell before their funds get stolen. Remember, Bitcoin’s market cap (and that of other cryptos) is not just held by cypherpunk hobbyists anymore; it’s held by hedge funds, ETFs, companies like Tesla, and even nation–states (El Salvador, for one).
首先諗下最壞情況:突然之間量子攻擊出現,對於未準備嘅比特幣網絡帶嚟衝擊。即刻輸家就係信心,對加密貨幣安全嘅信任一夜消失。主流幣價格即時急跌,用戶爭相賣出想保住資產。記住,依家比特幣(同其他幣)唔單止由密碼朋克愛好者持有,仲有對沖基金、ETF、Tesla啲大公司,甚至係國家(例如薩爾瓦多)。
A collapse in Bitcoin’s price triggered by a security failure could send shockwaves through traditional markets as well, given the growing institutional exposure. We might see a broader financial contagion if, say, big investors have to write down crypto holdings or face liquidity issues. Panicked sell–off is the phrase that comes to mind.
如果因安全失效令比特幣崩盤,傳統金融市場都可能受到波及,因為機構參與愈來愈多。大機構可能要減值資產或遇到流動性危機,引發更廣泛金融連鎖反應。最貼切描述就係「恐慌式拋售」。
In that chaos, who would be the “winners”? Obviously, the attacker (if it’s an entity) gains potentially massive amounts of stolen crypto – but spending it or cashing out may be tricky if everyone’s watching the addresses and exchanges blacklist the stolen funds. More interestingly, any assets or projects that are quantum–resistant could suddenly be in high demand. For instance, a niche coin like QRL (Quantum Resistant Ledger) might surge as people flock to something they perceive as safe. Companies offering post–quantum encryption solutions could see a boom in business (their services needed to secure exchanges, wallets, etc.). It’s also possible that alternative stores of value like gold or fiat currencies might get a relative boost as crypto temporarily loses shine.
咁喺亂局下有冇「贏家」?當然,個攻擊者(如果係某個人或者組織)一時間可以攞到好多被盜幣——但要洗錢同套現就難,因為大家都盯住區塊鏈地址,交易所會黑名單晒啲贓款。仲有,有啲抗量子資產或者專案突然會爆紅,好似QRL(Quantum Resistant Ledger)咁可能急升,因為大家會追落去避險。提供後量子加密方案嘅公司都會生意興隆(交易所同錢包都要搵佢哋打造安全措施)。金同法定貨幣呢啲其他價值儲存方式,亦可能因為加密貨幣暫時失寵而受益。
However, longer term, the term “winners” is hard to assign because if confidence in cryptography is broadly shaken, everyone is in trouble. As cryptographer Michele Mosca warned, if quantum cracked our cryptosystems unexpectedly, “confidence in digital infrastructures would collapse.”
但長遠嚟講,所謂「贏家」都難下定論。因為如果大家對密碼學都冇晒信心,其實冇人真係贏得到。就好似密碼學家Michele Mosca都警告過,如果加密系統突然比量子破解,「對數碼基建嘅信心會全面崩潰。」
We’d shift from orderly migration to “crisis management,” which “won’t be pretty,” he said. That extends beyond crypto: think of secure communications, banking, the internet. So one could argue the only real winners would be those who foresaw it and prepared, thus avoiding disruption. Among crypto players, that could mean communities that upgraded in time or designed with quantum in mind from the start.
屆時情況就會由有計劃咁慢慢轉型,變成「危機管理」,結果一啲都唔靚麗。呢啲影響唔只限於加密貨幣,仲有安全通訊、銀行、甚至整個互聯網。所以,真正嘅贏家係早有準備同主動防範嘅人。對crypto圈嚟講,即係啲及時升級或者一早已為量子風險設計嘅幣種或社群。
Let’s entertain a scenario where Bitcoin, through great effort, manages to migrate smoothly to post–quantum crypto before a quantum attacker arrives. In that case, Bitcoin’s network might sail through the “quantum scare” era and come out the other side robust. Its value proposition would actually strengthen (“Bitcoin survived the quantum transition!” would be quite the headline). Late–upgrading or stagnant projects could lose out. For example, if Bitcoin upgrades and some Bitcoin forks or smaller coins do not, users would likely abandon the weaker ones. One could imagine an investor rotation: moving capital from any coin perceived as lagging in quantum safety into those leading the pack. It’s a bit like Y2K for finance – companies that fixed their software in time were fine; those that ignored it risked failure.
假設比特幣經過大家齊心努力,趕喺量子攻擊者未出現前順利完成升級。咁比特幣網絡就可以帶住「量子大逃亡」呢段災難順利生還,而且價值主張反而會更強(「比特幣成功捱過量子衝擊!」一定成為頭條)。啲唔upgrade或者原地踏步嘅項目會被淘汰。例如比特幣升級,啲比特幣分叉或者細幣唔升級,大家一定會走去安全D果邊。可以想像到資本輪動:資金由落後於抗量子進度嘅幣,流向領先嘅幣。好似金融界Y2K咁——及時修正嘅公司就冇事,唔理會嘅公司就會面臨失敗。
We also have to consider the possibility of government intervention. If a quantum crisis hit, regulators might step in harshly. They could temporarily halt trading on crypto exchanges (to prevent further losses), or even attempt to coordinate a global response – perhaps pushing a certain standard upgrade quickly. Governments that were already skeptical of crypto might use the incident as fodder: “See, this stuff wasn’t safe, and now look at the mess.” On the flip side, if the crypto community navigates the quantum challenge well, it could impress regulators about the industry’s maturity and resilience, potentially building trust.
仲要諗埋政府介入嘅可能性。如果出現量子危機,監管機構可能會強力介入。佢哋可能會暫停加密貨幣交易所交易(避免損失擴大),甚至協調全球應對——例如勁快推某個標準升級。一向唔信加密貨幣嘅政府會拎呢件事嚟做藉口:「你睇下,呢啲玩意真係唔安全,依家亂成咁啦!」相反,如果加密圈能夠順利應對量子挑戰,反而會令監管機構覺得呢個行業成熟同有韌力,有機會建立信任。
What about decentralized finance (DeFi) and smart contracts? Those systems rely on the underlying blockchain security. If Ethereum’s cryptography were compromised, for instance, all those DeFi contracts could be drained by quantum attackers forging transactions or stealing keys to multisigs. The entire DeFi ecosystem could unravel very fast – essentially a series of bank runs as every user tries to pull funds out before attackers do. Collateral values would plunge, liquidations cascade. It would make the DeFi hacks we’ve seen so far (usually due to bugs or key thefts) look minor by comparison. Again, projects that are proactive – say a lending platform that migrates to quantum–safe authentication for user withdrawals or a DEX that uses quantum–resistant keys for its admin controls – would fare better.
咁去到去中心化金融(DeFi)同智能合約呢?呢啲系統都靠底層區塊鏈安全。例如Ethereum加密技術一旦失守,所有DeFi合約都可能畀量子攻擊者偽造交易或盜取多簽金庫匙,分分鐘一夜清袋。成個DeFi生態圈即刻瓦解——會變成一連串的銀行擠提,每個用戶都趕住領錢走,快過攻擊者。抵押品瘋狂下跌,斷頭盤湧現。比起而家時不時出現但規模細好多嘅DeFi駭客(通常只是漏洞或被偷私鑰),呢啲簡直唔同級數。主動應對嘅項目會好過人,例如提前用抗量子認證做提款,或者DEX用抗量子管理密鑰等。
It’s worth noting some might find a silver lining or opportunity. For instance, crypto miners: if somehow only a few parties have quantum tech for mining, they could reap outsized rewards (until difficulty adjusts or the network responds). But realistically, if mining was dominated by a quantum computer, that chain is effectively broken because decentralization is gone. So that’s not so much a winner as a Pyrrhic victory for one entity.
都應該講下可能有人覺得可以「搵著數」。例如加密礦工:如果只有幾個人有量子機去開採,初期或賺大錢(直到網絡調整難度或有反應)。不過現實點睇,如果礦工都畀量子電腦壟斷,成個鏈都係玩完,因為去中心化不復再。所以話唔算贏家,頂多算係「慘勝」。
Another angle: The insurance industry could face payouts if any insurers covered crypto losses due to theft (though many exclude such events). Alternatively, this could create a new market for “post–quantum insurance” and security services.
另一面,保險業都可能中招——如果有份保障加密貨幣失竊(雖然多數唔包呢啲),就要賠大錢。或者會誕生新興「後量子保險」同保安服務市場。
Economically, a quantum event hitting crypto could temporarily diminish the value of the whole sector – possibly by trillions in lost market cap in a severe scenario. But human ingenuity doesn’t stop. If people still see utility in cryptocurrency (and they likely will – the need for decentralized value exchange won’t vanish), the industry will rebuild on new, stronger foundations. Perhaps we’d see “Crypto 2.0” narratives with fully quantum–secure blockchains and maybe even quantum technology harnessed for new features.
從經濟角度睇,量子危機一下搞到加密貨幣,整個圈子暫時市值隨時縮水幾萬億都唔奇。但人類創意唔會消失。如果大家仲覺得加密貨幣有用(應該會——去中心化價值轉移永遠有需求),業界會基於更強安全度重建搞好。可能會出現「Crypto 2.0」新故事,全線抗量子區塊鏈,甚至將量子技術用嚟實現新功能。
In summary, in a quantum disruption:
總結一下,如果出現量子大動盪:
-
Losers: Anyone holding unprotected crypto (which is most of us, currently), exchanges and financial institutions entangled with a falling market, and generally trust in the system. Also, technically, quantum computing companies might face backlash for unleashing chaos, though they’d also have a boom in interest for solutions.
-
Winners: Those who hedged by investing in PQC early, quantum–resistant projects, possibly early adopters of upgraded coins, and the attackers (if malicious) until they get caught or their loot is rendered worthless by emergency forks or
-
輸家:手持無防護加密幣嘅人(即係大部份人)、捲入暴跌市場嘅交易所同金融機構、以及對整個系統嘅信任。另外,搞量子電腦嘅公司都可能因釋放混亂而被針對,雖然同時佢哋會因解決方案而受關注。
-
贏家:早早投資PQ加密、抗量子項目嘅人,早用新版本加密幣嘅玩家,同埋攻擊者(如果係惡意),直到佢哋被捉或者啲贓款被緊急分叉搞到冇用為止。blacklisting.
長遠來講,如果加密生態系能夠成功適應,最大得益者可能就是它本身——因為這代表它能夠展示出適應力,並且在目前為止最嚴峻的威脅之下獲得新生。不過,這個過程可能經歷經濟上的波動。老話一句,「預防勝於治療」在這裡尤其貼切。只要投入資源在預防措施(例如升級算法、做好私鑰管理、不重複使用地址等),加密社群就可以避免事後補救所帶來的更大痛苦。
量子就緒項目與未來展望
向前看,量子運算和加密貨幣的結合,既帶來威脅,同時也是機遇。這刺激了整個行業投入創新和資金,推動密碼系統變得更堅固。我們之前提過一些項目(QRL、Naoris、Quranium),它們標榜自己是「量子就緒」。這類項目現在看似小眾,但已經為我們展示量子時代下加密生態的可能運作方式。
例如,QRL 採用 XMSS 基於雜湊的簽名,就算真的有量子電腦出現,也不容易在 QRL 偽造交易,因為它的安全性主要依靠密碼學雜湊函數,這方面對量子攻擊(Grover 算法那種只有平方加速)來說相對安全。同樣,Quranium 採用無狀態雜湊簽名(可能類似於 SPHINCS+),完全不依賴傳統橢圓曲線或 RSA。
放眼整個行業,近期針對後量子密碼學初創團隊及研究組織的資金投入有明顯增加。美國及其盟友成立了 PQCrypto 等倡議,推動新標準落地。歐盟則在 Horizon 基金下資助本地量子安全密碼項目。風投也十分關注:研發量子安全 VPN、安全通訊、區塊鏈應用的公司開始獲得融資,市場普遍預期隨着量子運算技術實用化,這需求會爆升。情景有點像網絡安全萌芽之初——誰最快建好「量子防火牆」,就最有機會大賺一筆。
有趣的是,部分區塊鏈項目甚至研究量子運算的潛在好處。例如,有理論認為量子電腦某日能更有效運作特定工作量證明(Proof-of-Work)算法(雖然一般認為這是威脅,因為會令挖礦變得更集中),另一種潛在正面用途是「真正隨機數生成」。量子過程本質上是隨機的,部分協議可以利用量子隨機數生成器來改善共識或密碼協議中的不可預測性(譬如 Cardano 團隊曾提過用量子 RNG 增強領袖選舉的隨機性)。
再者,假如量子電腦終能有效解決某些優化問題或模擬化學反應,專注於相關領域的區塊鏈網絡(如計算或科學應用)亦有機會納入量子運算功能(如將量子計算 Oracle 或鏈下運算接駁智能合約)。
對一般加密用戶而言,未來展望毋須驚慌,但確實要提高警覺並作好準備。今日可行的做法之一:避免重用地址。正如 Nic Carter 強調,基本的 hygiene 好習慣——例如唔重複使用同一個比特幣地址——可令你的公鑰不會長時間暴露就手,提高安全性。換句話說,即使明天就有量子電腦問世,如果你的資產在一個從未動過的地址上,安全性會高一點(直到你用那個地址支出為止)。未來錢包相信也會開始提供量子安全地址選項。
舉個例,如某比特幣錢包未來推出可建立 P2QRH 地址(如果 BIP–360 或類似計劃通過),仲可一按幫你遷移資金。作為用戶,留意這些發展動向非常重要。未來可能會見到提醒你「立即升級錢包以轉用量子抗性地址」的提示,此時切勿拖延,應盡快跟進。
另一個方法是分散配置部份資產到本身具備量子抗性的加密資產。即,可以將少量幣放在量子安全的區塊鏈,甚或非數字類資產作為對沖。不過,以現時發展來看,只要主流加密貨幣有充足時間升級,用戶未必需要「棄船求生」。
從社群角度來說,未來幾年密碼學家、區塊鏈開發者、量子物理學家等跨領域合作只會愈來愈多。這個問題跨越多個學科。未來大概會有以區塊鏈和後量子安全為主題的工作坊、hackathon,IEEE、IACR 等組織已經積極推動跨界溝通。這種跨學科合作極之關鍵,因為要將 PQC 落實到區塊鏈,既要掌握新數學,亦要適應現實網絡環境。
最後,未來展望其中一個情景是:量子電腦出現時,加密貨幣唔單止可以生存,甚至變得更強。如果區塊鏈成功過渡到量子抗性算法,反而可能大大提升可信度,通過了韌性最終極的考驗。進一步來說,更有機會開闢量子驅動的密碼新範式。譬如零知識證明等進階協議有望藉助量子技術提升效能(已經有理論探討量子零知識證明)。
甚至有機會想像未來某天區塊鏈用上量子糾纏達成共識(聽落遙不可及,但概念上非常有趣:例如可否利用量子通訊令節點同步時有嶄新保證?)。這些想法雖然遙遠,但卻展示出:量子計算除了帶來威脅,亦可能為密碼信任帶來創新動力,只要用得其所。
總結來說,加密社群正以積極主動的姿態迎接「量子勢不可擋」的未來。新興項目已經領頭以量子抗性設計,主流網絡亦陸續規劃遷移路線。用戶無需明白 qubit 的物理原理都能受惠;只需繼續保持好習慣和及時更新軟件以獲得更強保障。加密貨幣一路以來都以韌性見稱——從交易所被黑、熊市、監管打壓到協議漏洞,無一倖免。量子挑戰只是這段旅程的其中一章。難度確實高,但只要及早適應和建立全球標準,產業不只可以應對,更有機會變得比從前更加堅固安全。
最後想法
量子運算和加密貨幣可以說是蓄勢待發、終將交鋒——可能唔係今日或明日,但遲早發生。一直以來這種衝突總是被形容得極之戲劇化:「量子運算會終結比特幣。」但根據前面的探討,其實我們需要一個更細緻的觀點。冇錯,某一天量子電腦會破解現時保護數位資產的特定密碼原語。但這並唔等於加密貨幣或數位安全就此終結。反而是新一章的開始——大家會部署更強盾牌,甚至用「量子武器」守護自己。
準備一切為先。這情景很像當年互聯網初起,網安威脅崛起——早認清黑客風險和投資網安的人獲得大成,而其他人只好付出昂貴學費。對加密貨幣行業來講,教訓非常明顯:唔好自滿。我們目標不是添煩添亂,亦唔想煽動恐慌(希望上文並未危言聳聽),只是想強調一個現實:現在正正有個時機窗口,確保加密貨幣即使面對可破解現有防線的量子電腦時,仍然「打極唔破」。
這份準備需要全球標準和協作。好似 NIST 曾經領導多年國際 PQC 標準化一樣,區塊鏈社群可能都需要自己的版本——比如橫跨多個項目、學界、甚至政府的量子抗性方案聯盟或工作小組,大家一起同步知識、協調進度,避免出現零碎、部分幣種安全、其他卻漏洞百出的情況,引起系統性連鎖問題。
同時,還需要大量教育和溝通。開發者要解釋為何需要某些升級(事實上歷史上不少重要升級就是因為誤解拖慢進度)。關於量子風險的溝通也要拿捏好,一來不能輕描淡寫,二來唔好太早「喊狼來了」令人麻木。正確的訊息應該是:「這是密碼學必然的演進,我地已經有解決方法——關鍵是如何有序、盡快地落實。」
可喜的是,現時不少頂尖密碼學家、電腦科學家已經積極投入這場戰役。邁向後量子年代,好多時被比喻成由 32-bit 過渡到 64-bit,或由 IPv4 過渡到 IPv6:只要有計劃,是重大的、但可控的轉型。最理想情況下,2035 年的普通加密用戶或許已經完全忘記曾有量子威脅——他們繼續照舊用比特幣、以太坊,背後已是晶格或雜湊簽名保護,一切如常。要達到這個「無事發生」的結局,就要依靠我們多年不懈的努力。right now (and perhaps some luck that quantum doesn’t
arrive notably sooner than expected).
此刻(亦可能要有啲運氣,即係量子電腦唔會比預期快咁多出現)。
In concluding, it’s fitting to echo the sentiment that often comes from level–headed experts: don’t panic – prepare. Just as long–term Bitcoin holders think in terms of years and decades, the network’s security must be thought of in generational terms. Quantum computing is a once–in–a–century kind of technological shift. Navigating it will require interdisciplinary cooperation: cryptographers to design the algorithms, blockchain engineers to integrate them, business leaders to fund and implement them, and yes, quantum scientists to keep us informed about the true state of the technology (beyond the hype). This is not a challenge any one group can tackle alone.
總結而言,好適合引用一班冷靜專家經常提到嘅意見:唔好驚——要準備好。正如長期持有比特幣嘅人用年同年代嚟思考,整個網絡嘅安全都要用幾代人嚟規劃。量子運算係百年一遇嘅重大科技變革,需要跨界協作先可以安全應對——密碼學家要設計新演算法,區塊鏈工程師要整合,新創企業領袖要籌錢同落實,當然,仲需要量子科學家為大家更新真正技術進展(唔只係炒作)。呢場挑戰,唔可能淨係靠一個圈子處理到。
The cryptographic cat–and–mouse game will continue as it always has. Quantum computers will force cryptography to evolve, and evolve it will. Blockchains, if they are to be the permanent fixtures of value exchange that many hope, must evolve too. In the end, the story of “unbreakable becomes breakable” might flip to “breakable becomes unbreakable again.” By getting ahead of the threat, the crypto community can ensure that its foundational promise – security without centralized trust – holds true, even against the most powerful computers humanity ever builds. The era of quantum computing will be an era of reckoning and then, hopefully, an era of renewal for crypto security. The time to start building that future is now.
密碼學界嘅「貓捉老鼠」遊戲會繼續落去。量子電腦必然會迫使密碼學不斷進化,而密碼學都必然會應變。區塊鏈,如果真係要成為永久價值交換平台,都一定要迎難而上。到最後,「不可破解變得能破解」嘅故事,可能會翻轉做「能破解都變返不可破解」。只要領先危機一步,加密社群就能確保其核心理念——「去中心化信任下實現安全」——能夠成立,就算面對史上最強電腦都頂得住。量子運算時代會先帶嚟一次大審視,希望最終就會迎來加密安全新生。要打造呢個未來,宜家就要開始行動。



