In recent years, advances by companies like IBM and Google have pushed quantum computing from theory toward reality, reigniting debate in the cryptocurrency community about its implications. IBM’s latest quantum processors now pack over 400 qubits, and the company claims a “clear path” to full–scale quantum machines by the end of this decade. Google is similarly optimistic, saying the remaining engineering challenges to large–scale quantum computing are “surmountable,” with milestones being reached at a rapid clip.
This progress has not gone unnoticed in crypto circles: forums and experts are buzzing about when quantum computers will become powerful enough to threaten the cryptography that underpins Bitcoin and other blockchains. Some, like Solana co–founder Anatoly Yakovenko, even warn there’s a “50/50” chance of a major quantum breakthrough by 2030 and urge the Bitcoin community to “speed things up” in preparing defenses. Others are more skeptical, noting that truly “useful” quantum computers may still be 15–20 years away, as NVIDIA’s CEO Jensen Huang recently predicted.
What’s clear is that quantum computing is no longer an abstract, far–off idea – it’s a developing technology with real implications for cybersecurity. And that brings both threats and opportunities for the crypto world. On one hand, a sufficiently advanced quantum computer could break the “unbreakable” cryptographic shields protecting digital assets. On the other, the race toward quantum–resistant encryption is spurring innovation and could ultimately strengthen blockchain ecosystems that adapt in time.
This explainer will delve into all sides of the issue: why quantum computing poses a unique threat to cryptocurrencies, how it could crack Bitcoin’s encryption, when experts think that might (or might not) happen, and what the industry is doing to prepare. We’ll also explore hypothetical scenarios – like what if a quantum attack on Bitcoin happened tomorrow – and consider the long–term fallout: Who would win, who would lose, and how might the crypto economy change when the “unbreakable” becomes breakable?
Crucially, this isn’t a doom–and–gloom prophecy. It’s a sober examination of a potential future risk – one that may be years or decades off, yet demands proactive planning today. By understanding the threat without the hype, crypto developers and users can take steps now to ensure that when quantum computing finally arrives at scale, the crypto ecosystem is ready to bend, not break.
How Quantum Computing Works (Without the Hype)
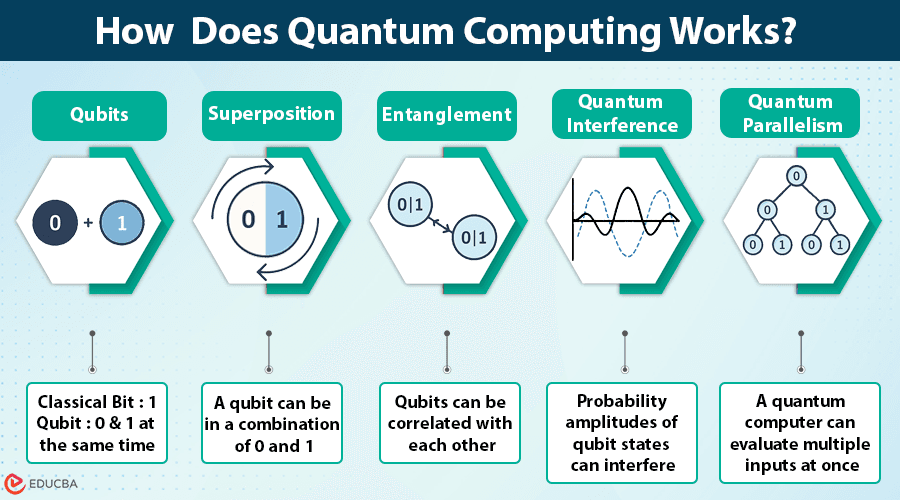
Quantum computing is fundamentally different from the classical computers we use today. Rather than the binary bits (0 or 1) of classical computing, a quantum computer uses quantum bits, or qubits, which can exist in multiple states at once thanks to a phenomenon called superposition. In simple terms, a qubit is like a coin flipping in the air – it’s not just heads or tails, but potentially both until observed. Qubits can also become entangled with one another, meaning the state of one qubit can depend on the state of another even across distance. This allows quantum computers to process a vast number of possibilities simultaneously. When you string many qubits together and interfere with their probability waves in just the right way, you can perform certain calculations exponentially faster than a normal computer could.
It’s important to cut through buzzwords often thrown around in this field. You might have heard the term “quantum supremacy.” This refers to a quantum computer performing a task that no classical computer can feasibly solve in any reasonable timeframe. Google famously claimed to have achieved quantum supremacy in 2019 when its 53–qubit Sycamore processor performed a specialized computation in minutes that Google estimated would take a supercomputer 10,000 years. (IBM later argued a supercomputer could do it faster with an optimized method, but the milestone was significant nonetheless.)
A related term is “quantum advantage.” While quantum supremacy is about outperforming classical machines at any task (even a contrived one), quantum advantage implies a quantum computer solving a practical, useful problem better or faster than a classical computer. In other words, supremacy was a proof of concept; advantage will be when quantum computing starts doing things that matter in the real world, like material science simulations or complex optimizations that classical computers struggle with.
Today’s quantum machines are still in their infancy. They are noisy and error–prone, meaning qubits easily lose their delicate quantum state (a problem called decoherence). The number of qubits is also still relatively small. For instance, IBM’s cutting–edge Osprey processor, unveiled in 2022, contains 433 qubits – a record at the time. For perspective, researchers estimate it may take on the order of a million high–quality qubits to crack modern encryption like Bitcoin’s (more on that shortly). In the image below, IBM’s Osprey quantum processor (rendering) is shown – it was a major leap, but still far from the scale needed to threaten Bitcoin’s cryptography.
Even IBM’s head of quantum hardware has noted that reaching “truly useful” quantum computers likely requires new architectures to link chips together into larger, modular systems.
A 3D rendering of IBM’s 433–qubit “Osprey” quantum processor, introduced in 2022. Quantum processors like this mark significant progress in qubit count, but experts say millions of error–corrected qubits would be required to break the cryptography protecting Bitcoin and other cryptocurrencies. (Image: IBM/Connie Zhou via Reuters)
So, while quantum computing is advancing quickly, it’s not magic. We haven’t reached a point where a quantum laptop can sit on a desk and crack any code in seconds. The “quantum supremacy” demonstrations so far, including those by Google and Chinese researchers, involved highly specialized tasks with minimal real–world impact. “Quantum advantage” in practical applications is the next goalpost, and even optimistic projections put that a few years ahead.
For now, quantum computers remain lab experiments and cloud–based prototypes, mostly tackling niche problems. However, their trajectory is clear: capabilities are improving, and the moment they can solve useful problems classical computers can’t, the ripple effects will be felt across many industries – including crypto.
Why Bitcoin’s Encryption May Not Be Forever
Bitcoin often gets described as “unhackable,” and so far its core cryptography has lived up to that reputation. At the heart of Bitcoin’s security is the Elliptic Curve Digital Signature Algorithm (ECDSA), a cryptographic scheme dating back to the 1980s that allows a user to prove ownership of funds. Here’s how it works: you control a secret number called a private key, and from that private key you can derive a public key by multiplying it against a fixed elliptic curve (a kind of mathematical one–way function).
The public key can be shared widely – it’s hashed to form your Bitcoin address – while the private key remains known only to you. If you want to spend your bitcoin, you create a digital signature with your private key; the network uses your public key to verify that signature and thus authenticate the transaction.
Critically, this process is a one–way street: given the public key, there is no known feasible way for a classical computer to calculate the corresponding private key. As Bitcoin researcher Nic Carter put it, Bitcoin’s entire security model rests on the assumption of a one–way math problem that’s “easy to compute in one direction, and infeasible to invert” with classical computing. In practice, trying to brute–force someone’s 256–bit private key with an ordinary computer would take billions upon billions of years – effectively impossible.
Quantum computing threatens to upend this asymmetry. In 1994, mathematician Peter Shor discovered a quantum algorithm (aptly named Shor’s algorithm) that can efficiently solve the kind of math problem underpinning ECDSA. Specifically, Shor’s algorithm can perform prime factorization and compute discrete logarithms exponentially faster than any known classical algorithm. The discrete log problem on elliptic curves (which secures ECDSA) is closely related to these tasks. In plain language, a future quantum computer running Shor’s algorithm could derive a Bitcoin private key from its public key, breaking the fundamental security of ECDSA.
All an attacker would need is the victim’s public key – which, in Bitcoin, typically becomes visible on the blockchain whenever that user makes a transaction. Once a quantum attacker can compute the private key, they can spend the coins in that wallet at will. The “unbreakable” cryptography would suddenly be quite breakable. David Carvalho, CEO of cybersecurity firm Naoris Protocol, explained that if this ever happened, it would appear as if wallets were being accessed legitimately: “Everything would look like legitimate access… You wouldn’t even know” a theft was quantum–driven, because the thief would produce valid signatures just like the true owner.
It’s not just the signature algorithm at risk. Bitcoin also relies on cryptographic hash functions, chiefly SHA–256, in its mining process and address generation. While hash functions aren’t as directly threatened by quantum algorithms as public–key cryptography is, they’re not entirely immune. Quantum computers could use Grover’s algorithm to speed up the search for a hash collision or a specific pre–image. Grover’s algorithm provides a quadratic speed–up for brute–force search problems.
In the context of Bitcoin mining (which is essentially a brute–force race to find a SHA–256 hash below a certain target), a quantum computer with Grover’s algorithm could theoretically mine significantly faster than classical computers. Fortunately, Grover’s advantage is not as devastating as Shor’s. It would effectively halve the strength of a hash algorithm: SHA–256, which has a 256–bit output, would have its security reduced to about 128–bit under quantum attack. A 128–bit security level is still quite strong – by comparison, 128–bit AES encryption is considered military grade today.
However, if quantum hardware becomes powerful, even that quadratic speed–up could give an overwhelming advantage to a quantum–equipped attacker in Bitcoin mining, potentially leading to a 51% attack or other disruptions. It’s a less immediate threat than breaking signatures (since mining difficulty and other factors can adjust), but it’s part of the worry.
In summary, Bitcoin’s cryptography was designed in an era when only classical computers existed. The designers assumed certain math problems were practically unsolvable (like finding a private key given a public key). Quantum computing flips that assumption on its head. With enough qubits and the right algorithms, what was once infeasible could become feasible. “Bitcoin needs to protect people’s funds over generational timescales,” as cryptographer Ethan Heilman noted – meaning it must withstand not just today’s computers but tomorrow’s as well.
The harsh truth is that the encryption securing Bitcoin and many other cryptocurrencies “may not be forever” in the face of quantum progress. That’s why this issue, long discussed in theory, is now being taken more seriously as quantum labs inch closer to machines capable of breaking ECDSA and other legacy crypto.
The “Quantum Attack” Scenario: What If It Already Happened?
One chilling aspect of a quantum attack on Bitcoin is that it could unfold in silence, without obvious signs of intrusion. If a quantum computer powerful enough to crack Bitcoin’s keys came online today, it’s possible coins could start moving from wallets and nobody would immediately realize those transactions were fraudulent. “If a quantum computer capable of breaking modern encryption were to come online today, Bitcoin would likely be under attack – and no one would know,” Carvalho warned in an interview.
That’s because a quantum thief doesn’t need to hack the network or create counterfeit coins; they simply break the private keys of targeted accounts and use them to generate valid transactions. To the blockchain, these transactions look just like any other user signing with their key.
Imagine waking up to see that an early Bitcoin address – one that hasn’t been touched in a decade – suddenly sent all its BTC to an unknown wallet. On–chain analysts might wonder if a long–lost holder finally came back, but in a quantum theft scenario, it could be an attacker who computed the private key for that address and drained it. The blockchain would continue chugging along normally, blocks getting mined and transactions confirmed, while behind the scenes the ownership of some coins had quietly changed hands. As Carvalho put it, “You’d just see those coins move as if their owners decided to spend them”. There’d be no failed signatures or obvious red flags in the ledger itself.
Which coins would be most at risk? Experts point to the oldest and most dormant wallets as prime targets. Kapil Dhiman, founder of post–quantum startup Quranium, noted that Bitcoin’s earliest addresses (including Satoshi Nakamoto’s legendary stashes) used less secure cryptographic practices by today’s standards.
For instance, many early coins are held in P2PK addresses where the public key is directly visible on–chain (as opposed to the modern P2PKH style that hides the public key behind a hash until it’s spent). “Satoshi’s coins would be sitting ducks,” Dhiman told Cointelegraph, referring to the roughly 1 million BTC believed to be mined by Bitcoin’s creator. If those long–idle coins suddenly moved, it would shatter confidence – people might assume either Satoshi returned or a quantum attacker struck, and either scenario would be hugely destabilizing.
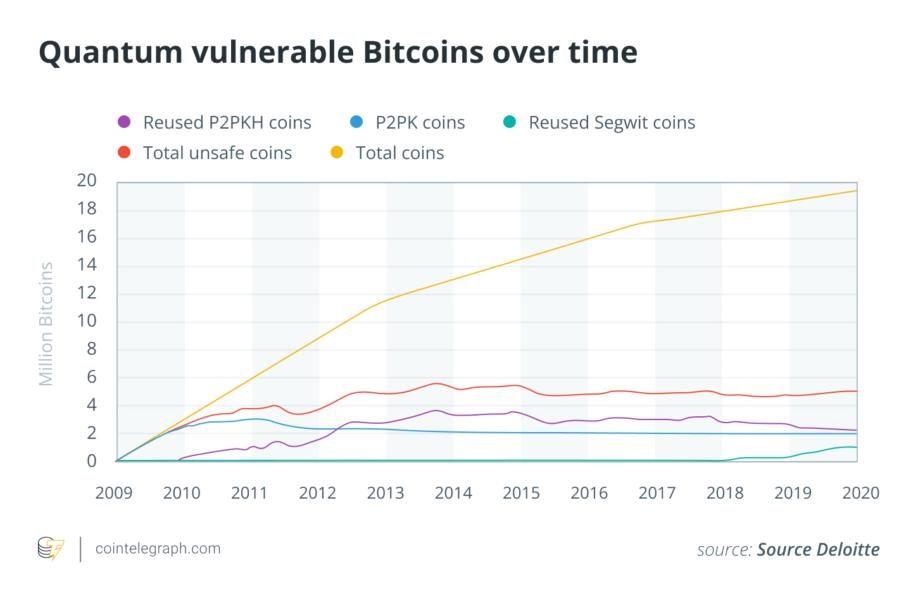
Aside from Satoshi, any wallet that has reused addresses or exposed its public keys falls into the vulnerable category. A study by Deloitte estimated that as of 2022, about 25% of Bitcoin in circulation could be considered “unsafe” against a quantum attack on signature algorithms. This includes coins in old–style addresses and any address that had been used more than once (thus revealing the public key). Conversely, roughly 75% of coins were in “safe” addresses (at least until those addresses are spent from). Over time, however, even safe addresses become unsafe once their owner makes a transaction, because the act of spending typically discloses the public key in the transaction signature.
What would the immediate fallout look like if stealthy quantum thefts began? Potentially, chaos. Users might notice high–value wallets being drained and panic–sell, causing price crashes. But attribution would be tricky – was it quantum hacking, or just a hacker who somehow got someone’s keys through more traditional means? By design, the evidence of a quantum attack could hide in plain sight. “When you think you’re seeing a quantum computer out there, it’s already been in control for months,” Carvalho warned, alluding that by the time the public suspects such an attack, the adversary could have already stolen a fortune quietly.
In a thought–provoking analogy, he compared it to the Allied codebreakers in World War II who cracked the Enigma cipher. They kept that breakthrough secret, even allowing some attacks to succeed, so as not to tip off the Germans that Enigma was compromised. A state–level actor with a quantum computer might similarly prefer to exploit Bitcoin’s cryptography covertly for as long as possible, rather than announce their capabilities.
It’s important to stress that as of today, this scenario remains theoretical. There is no public evidence that anyone has a quantum computer capable of such feats – “the consensus in the scientific, research and military communities is that it is not the case,” Carvalho noted. But he also added a cautionary note: “it would not be the first time world–class cryptography had been broken without public knowledge.” Until an adversary demonstrates it, we operate under the assumption that Bitcoin is safe.
Nonetheless, the mere possibility of an undetectable quantum attack is enough to warrant intense precaution. This is why some security experts treat the quantum threat not as science fiction but as an urgent engineering problem; as one researcher put it, “Have a plan.” If we wait until coins start mysteriously vanishing to react, it will likely be too late to contain the damage.
Timeline: How Close Are We to a Quantum Threat Reality?
The billion–dollar question: When might quantum computers actually become powerful enough to pose a real threat to Bitcoin’s cryptography? The answers you’ll get from experts range widely – from “maybe a decade or two” to “not in our lifetimes” to “sooner than you think.” The scientific consensus tends to put the threat at least 10+ years out, but with some big caveats and minority opinions.
A useful reference point is the work of national security agencies and standards bodies. The U.S. National Institute of Standards and Technology (NIST), which has been leading the charge on post–quantum cryptography, recommends organizations transition to quantum–resistant algorithms by 2035 as a precaution. This isn’t because they expect a cryptographically relevant quantum computer in 2035, but because of the so–called “harvest now, decrypt later” risk: adversaries could be recording encrypted data now (or gathering public keys from blockchains now) to decrypt once they have a quantum machine in the future.
NIST’s timeline implies that by the 2030s, quantum computers might be close enough to breaking some crypto that long–term data security could be in jeopardy. That said, some crypto insiders point out that Bitcoin might not face the same urgency as, say, encrypted communications. Charles Guillemet, CTO of Ledger, noted that NIST’s 2035 guideline is about forward secrecy (protecting today’s secrets against tomorrow’s decryption), whereas Bitcoin transactions aren’t meant to be secret in the first place. In his view, Bitcoin’s specific exposure is mostly limited to the scenario of on–the–fly key theft (rather than retroactively decrypting old messages), giving a bit more buffer time.
Looking at the state of quantum hardware: IBM’s roadmap envisions quantum processors with a few thousand qubits by 2033, still far below the millions of qubits likely needed to break Bitcoin’s 256–bit keys. To date, the largest announced quantum chip is IBM’s 433–qubit Osprey (2022), and IBM aims to cross the 1,000–qubit mark with a chip called Condor in 2023–2024, and keep scaling from there. Google, on its end, has talked about building a useful error–corrected quantum computer by the end of the decade (around 2029) – essentially a machine that could continuously run quantum algorithms reliably thanks to error correction.
These timelines are ambitious, but not guaranteed. Notably, even thousands of qubits are not enough to break Bitcoin; those qubits also need to be high–quality (low error) and the algorithms need to be optimized. One academic study estimated that a quantum computer would need on the order of 13 million qubits to crack a Bitcoin private key in 24 hours using Shor’s algorithm. Today’s count of 433 or even 1,000 qubits is a drop in the bucket by comparison.
Industry experts often temper the hype. In early 2025, Nvidia CEO Jensen Huang – whose GPUs are used in some quantum control systems – said “very useful quantum computers” are probably about 20 years away. “If you said 15 years, that’d be on the early side. If you said 30, probably the late side. Pick 20,” Huang elaborated, suggesting a long road ahead. Similarly, crypto pioneer Adam Back has been dismissive of claims that Bitcoin could be broken by 2028, stating “no way” and even musing about betting against such predictions. Back estimates maybe 20 years to worry.
Another well–known Bitcoiner, Samson Mow, commented that quantum computing is “a real risk, but the timeline is probably still a decade away”, adding that in his opinion “everything else will fail before Bitcoin fails” if such a threat materialized. These views reflect a common stance in the Bitcoin development community: cautious monitoring rather than immediate alarm.
However, there is a vocal contingent urging more urgency. Solana’s Anatoly Yakovenko, as mentioned, gives even odds to a breakthrough by 2030 and thinks it’s “astounding” how fast related tech like AI is advancing, suggesting quantum could surprise us on the early side. In mid–2023, a leaked Google Quantum AI roadmap implied a potential steep increase in qubit counts in coming years, fueling speculation.
And in the realm of national security, we can’t ignore the possibility of classified progress: government labs might not publicize every breakthrough, especially if it has intelligence value. That’s partly why cryptographer Michele Mosca coined the idea of “Q–day” – the day a quantum computer can break present cryptography. He and others warn that Q–day could arrive abruptly and ahead of schedule, catching those who assumed a slower timeline flat–footed.
All told, most estimates as of 2025 put the quantum threat to widely used cryptography in the 2030s or beyond. A report by Bernstein analysts, for example, still views the threat as “decades away.” But consensus can change with a single breakthrough. The community got a jolt in late 2022 when Chinese researchers claimed a new approach to factoring that, if scalable, might significantly cut the requirements for cracking RSA keys with a quantum hybrid method.
That particular claim was met with healthy skepticism and likely doesn’t pan out to a real attack, but it served as a reminder: advances can come from anywhere, and we might underestimate what’s possible. As theoretical computer scientist Scott Aaronson wrote, the prudent stance is “yes, unequivocally, worry about this now. Have a plan.” Early planning ensures that even if quantum decryption ability comes sooner than expected, the crypto world isn’t caught completely unprepared.
Post–Quantum Cryptography: What Solutions Exist?
The good news is that the cryptography community hasn’t been sitting idle waiting for Q–day. A field of research known as post–quantum cryptography (PQC) has been developing new algorithms that can withstand attacks from quantum computers. Unlike “quantum cryptography” (which often refers to using quantum physics for things like quantum key distribution), post–quantum algorithms run on classical computers but are designed to be difficult for a quantum adversary to crack.
In 2016, NIST launched an open competition to identify the best post–quantum algorithms, and after several rounds of evaluation, they announced the first batch of standardized PQC algorithms in 2022. These include:
- CRYSTALS–Kyber: a lattice–based key encapsulation mechanism (used for encrypting data or establishing shared secrets).
- CRYSTALS–Dilithium: a lattice–based digital signature scheme.
- FALCON: another lattice–based signature (offering smaller signatures at the cost of more complex implementation).
- SPHINCS+: a hash–based signature scheme that is stateless (doesn’t require tracking used keys).
By 2024, NIST had finalized standards for these algorithms (Kyber for general encryption, Dilithium and FALCON for signatures, and SPHINCS+ as an alternate signature) and published them as FIPS 203–205. In layman’s terms, if we swap out Bitcoin’s ECDSA and SHA–256 for some combination of these new algorithms, the network would be protected from known quantum attacks.
For example, instead of elliptic curve signatures, one could use a lattice–based signature like Dilithium or a hash–based signature like SPHINCS+. These algorithms rely on mathematical problems believed to be resistant to quantum algorithms (like the hardness of lattice problems or the security of cryptographic hash functions), so Shor’s and Grover’s methods wouldn’t be able to crack them in any reasonable time.
Implementing post–quantum cryptography on a blockchain, however, is easier said than done. PQC algorithms often have trade–offs: larger key sizes or signature sizes, slower performance, etc. A Dilithium signature, for instance, is a few kilobytes in size (compared to a compact 64–byte ECDSA signature), which could bloat blockchain transactions. A hash–based scheme like SPHINCS+ has even larger signatures and can be slower to verify, but it offers a very different security basis (it’s based on hashes, which we know and trust). Despite these downsides, the transition is feasible. We already see some crypto projects positioning themselves as quantum–resistant from day one.
For example, the Quantum Resistant Ledger (QRL) is a blockchain that launched with a built–in post–quantum signature scheme (XMSS, an extended hash–based signature related to SPHINCS+). QRL chose XMSS specifically to protect against future quantum attackers, even though it means each wallet address can only safely sign a certain number of times before the keys should be rotated (a quirk of stateful hash–based signatures). Another project, QANplatform (not mentioned above, but known in the industry), claims to use lattice–based cryptography to secure its smart contract platform.
Quranium, led by Kapil Dhiman, uses a NIST–approved stateless hash–based digital signature scheme to secure its Layer–1 blockchain. And earlier we heard from Naoris Protocol’s David Carvalho – his project is building post–quantum infrastructure and was even cited in a proposal to the U.S. SEC discussing quantum security standards. These niche projects are still relatively small, but they serve as proving grounds for PQC in blockchain environments. They also provide a sort of insurance: if the big networks were slow to adapt and quantum cracking arrived, theoretically one could move value into a quantum–resistant chain like QRL to safeguard it (assuming an orderly scenario).
Major blockchains have also been researching solutions. Ethereum, for instance, has had discussions and prototype implementations of quantum–resistant cryptography. Ethereum developers explored lattice–based signatures and even post–quantum variants of zk–SNARKs (zero–knowledge proofs that are transparent to quantum attacks). There’s an Ethereum Foundation research post on using lattice–based BLS signatures in a post–quantum context. So far, none of this is live in production – Ethereum’s current use of ECDSA and BLS (for validators) remains as vulnerable as Bitcoin’s in principle. But the groundwork is being laid.
Beyond digital signatures, there’s also the question of quantum–proofing the mining or consensus process. Bitcoin’s proof–of–work could theoretically be hardened by moving to a longer hash (SHA–512 or something) if Grover’s algorithm became a practical threat. Some have even suggested switching Bitcoin from proof–of–work to proof–of–stake before quantum computers arrive, under the argument that PoS doesn’t rely on a brute–force race in the same way (though PoS has its own cryptographic assumptions to consider). These ideas are speculative, and Bitcoin’s community is generally very conservative about such fundamental changes.
Another intriguing line of defense is using quantum cryptography itself. For example, quantum key distribution (QKD) uses quantum physics to let two parties generate a shared secret key with the guarantee that any eavesdropping will be detected. QKD isn’t directly applicable to public blockchains (which are decentralized and don’t have point–to–point links), but institutions could use it to secure communication channels in a blockchain system.
In 2022, JPMorgan Chase and Toshiba demonstrated a blockchain network secured with QKD to fend off quantum attackers intercepting data. They basically layered quantum–secure communication on top of the blockchain. This kind of approach might see more use in private ledgers or inter–bank networks. However, for public cryptocurrencies, the focus is firmly on upgrading the algorithms themselves to PQC.
So, to recap the solutions landscape: We have a toolkit of post–quantum algorithms ready or nearly ready for deployment, thanks to years of research and vetting by NIST and others. We have early movers in the crypto industry implementing these defenses on alternative platforms. And we have proposals (which we’ll discuss next) for how the incumbents like Bitcoin could gradually migrate. The technical pieces exist to keep crypto safe in a post–quantum world. The bigger challenges might be social and logistical: how to coordinate a switchover of millions of users and critical infrastructure. As one cybersecurity CEO, Chris Erven, remarked, “the time has come for quantum–safe technology to be at the heart of cybersecurity strategies globally” – it needs to be embedded proactively, not slapped on at the last minute.
Comparing Crypto and TradFi Progress
When it comes to preparing for quantum threats, the world of traditional finance and government may actually be moving faster than the crypto industry. Large banks, enterprises, and agencies have the advantage of centralized control – they can mandate security upgrades top–down. Cryptocurrencies, by contrast, are decentralized by design, which makes coordinated transitions more complicated.
Take the banking sector: JPMorgan Chase has been notably proactive. In addition to the quantum key distribution experiment mentioned earlier, JPMorgan has a “Future Lab” for quantum technologies. Marco Pistoia, who leads that lab, said the bank is preparing “for the introduction of production–quality quantum computers” precisely because they could “change the security landscape of technologies like blockchain and cryptocurrency in the foreseeable future”. JPMorgan isn’t waiting for an emergency; they’re testing defenses now. Similarly, the global banking network SWIFT has launched training programs and workshops on post–quantum security for its member institutions.
Companies like IBM and Microsoft are already offering quantum–safe encryption options in their cloud products, so that companies can start encrypting data with algorithms like Kyber or Dilithium ahead of time. The U.S. government passed the Quantum Computing Cybersecurity Preparedness Act (in late 2022), which requires federal agencies to begin planning to migrate their systems to post–quantum cryptography. In 2015, even the NSA (which historically helped curate US encryption standards) announced plans to transition to quantum–resistant algorithms – a strong signal to industry and academia to get moving.
Now compare that to the state of most cryptocurrency networks: Bitcoin, Ethereum, and the majority of altcoins still use RSA, ECDSA, or EdDSA signatures and standard hashing (SHA–2, SHA–3, etc.). There has been no urgent migration yet. Part of the reason is that, as we discussed, many in the community believe the threat is not imminent. Another part is the challenge of consensus: to change Bitcoin’s signature algorithm, for example, literally every participant in the network needs to agree (or at least a supermajority, if done via soft fork).
That’s a slow process involving proposals, coding, testing, and convincing the global user base. “Traditional finance is actually ahead,” as Naoris’ Carvalho observed. “They have central control, budgets and a single authority that can push upgrades. Crypto doesn’t have that. Everything takes a consensus.” In other words, Jamie Dimon can tell JPMorgan’s security team “we’re switching all internal communications to post–quantum encryption next year” and it’ll likely happen.
There’s no analogous figure in Bitcoin who can unilaterally decree a crypto upgrade – by design, it’s nobody’s call alone. We’re seeing some movement in the crypto space though. The fact that Bitcoin developers are drafting quantum–mitigation proposals now (in 2023–2025) shows the gap is understood. And some crypto companies are getting involved in the broader PQC effort. For instance, blockchain security firms and academic collaborations are exploring crypto–agility – designing protocols that can swap out cryptographic primitives more easily in the future. The ideal scenario is to make blockchain networks as nimble as web browsers, which can (in theory) roll out new cryptography via updates when needed. But getting millions of decentralized nodes to update is a bigger undertaking than updating, say, Google Chrome or Firefox on user devices.
Another point of contrast is the risk surface. Traditional finance relies heavily on encryption for secure communication (TLS for banking websites, VPNs, secure messaging, etc.), all of which could be undone by a quantum attacker. So banks face not only the threat of cryptocurrency theft but also potentially the exposure of sensitive customer data and financial transactions if encryption breaks. This gives them a broad incentive to upgrade everything encryption–related.
Cryptocurrencies have a narrower but more acute risk: the integrity of the currency itself. A quantum attack on crypto doesn’t reveal confidential information (since blockchains are public), but it could undermine ownership and trust in the system. In some sense, the crypto risk is “all or nothing” – either your coin’s algorithm gets broken and chaos ensues, or it doesn’t. Banks meanwhile might survive some breaches but face massive privacy or financial losses if they drag their feet on PQC.
Interestingly, some collaborations are emerging between tradfi and crypto on this issue. JPMorgan’s quantum–safe blockchain network could be seen as a private blockchain use case, but the tech could potentially inform public chains too. IBM, being a major player in both enterprise blockchain and quantum computing, might eventually help bridge solutions into the open–source blockchain world. And governments might impose standards – for example, one could imagine a future regulation that says any cryptocurrency used by banks or traded on regulated exchanges must be quantum–resistant by a certain date. That would light a fire under the decentralized projects to adapt or face delisting.
In summary, the traditional finance world has started the post–quantum transition in earnest, leveraging their centralized structure to do so. The crypto world lags behind not due to ignorance but due to the inherent difficulty of making protocol changes in a decentralized environment and a perhaps justified sense that the danger isn’t right at the doorstep yet. The challenge ahead is accelerating crypto’s migration pace without undermining the qualities (decentralization, stability) that make it valuable. It’s a delicate balance of not crying wolf too early versus not sticking one’s head in the sand. The next section will delve into how Bitcoin might approach this in practice, which illustrates just how complex that governance process can be.
What If Bitcoin Migrates? The Governance Challenge
Let’s say the Bitcoin community collectively decides, “Yes, we need to upgrade our cryptography to be quantum–safe.” How would that actually happen? This is where the governance challenge kicks in. Upgrading Bitcoin is often compared to repairing an airplane mid–flight – any change must be carefully designed not to break the system as it runs. For a quantum–resistant Bitcoin, developers have proposed a few routes, each with pros and cons.
One key proposal making rounds is known as BIP–360, also nicknamed “Bitcoin Post–Quantum” or “QuBit” (not to be confused with qubit, the quantum bit). BIP–360 is a draft Bitcoin Improvement Proposal by a pseudonymous author “Hunter Beast” that sketches a multi–stage plan to introduce quantum–resistant addresses and signatures to Bitcoin. The idea is to do it gradually to avoid chaos. Here’s a simplified rundown of the plan:
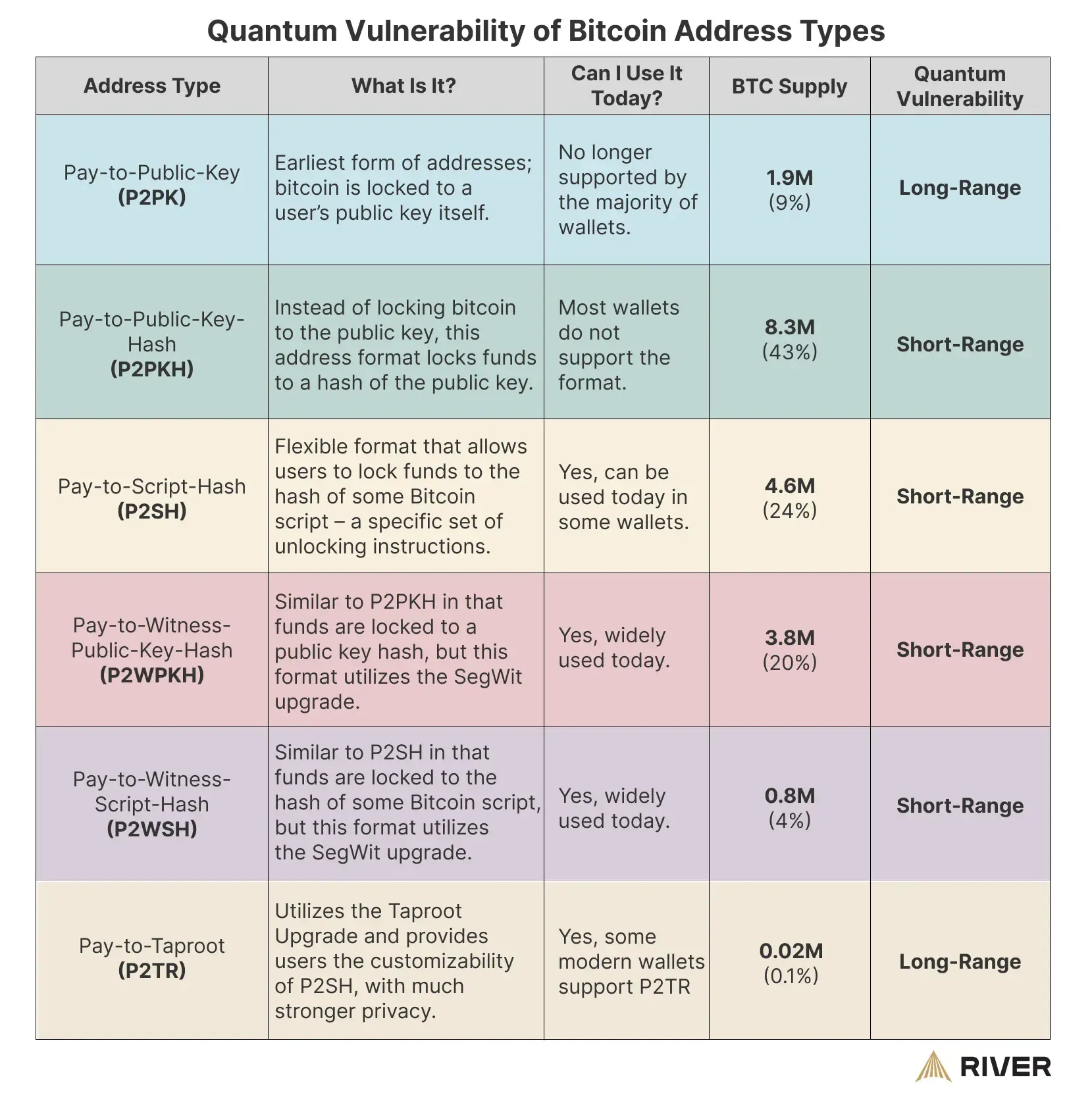
Stage 1: Introduce a new address format, called P2QRH (Pay–to–Quantum–Resistant–Hash), that can support various post–quantum signature algorithms. Users could start creating new addresses of this type and sending Bitcoin to them. These addresses would be backwards–compatible (they’d look like any other address to old nodes, likely via some versioning), so this can be done as a soft fork.
Stage 2: Once P2QRH addresses exist, give people an incentive to use them. QuBit proposes a block weight discount (16x cheaper in terms of fees) for transactions from quantum–resistant addresses. This is similar to how SegWit’s rollout gave discounts to encourage adoption. Cheaper fees would nudge wallets and users to migrate funds to the new address type over time.
Stage 3: Develop a Taproot–compatible version of these addresses, and eventually make a soft fork that begins to require quantum–resistant signatures for new transactions. At this point, perhaps after many years of voluntary adoption, the community might agree to “sunset” the old ECDSA–based addresses.
Stage 4: In the far future, once it’s confirmed that quantum threat is imminent, a final soft fork could disable old signature types entirely, making Bitcoin fully post–quantum for all transactions going forward.
This phased approach is meant to tackle governance pragmatically: don’t force everyone to switch on a dime (which would be a hard fork and contentious), but rather introduce the new system, encourage its use, and slowly make it the default. By using soft forks, backward compatibility is maintained – old nodes would see a P2QRH transaction as anyone–can–spend (if not aware of the new rules) but thanks to miner enforcement, it would still be secure. It’s complex engineering, but Bitcoin has navigated tricky upgrades like SegWit in the past.
There are some trade–offs and open questions. Quantum–resistant signatures are big, so if a lot of people start using them, it could effectively reduce how many transactions fit in a block (hence discussions of a block size increase have floated around in conjunction). QuBit’s current iteration suggests that using PQ signatures might effectively lower throughput somewhat, but it considers that an acceptable price for security. There’s also the matter of which quantum–safe algorithms to choose.
QuBit smartly doesn’t lock in one algorithm; it supports a few (like SPHINCS+–256F and FALCON–1024) and lets users pick. This hedges against any single new algorithm later being found flawed – a wise move given PQC is relatively new and not battle–tested like RSA/ECC. Still, more exotic options like lattice signatures could introduce their own uncertainties (e.g., if a breakthrough math attack on lattices happened, that could be an issue; it’s not likely, but it’s the kind of thing cryptographers consider).
An alternative strategy is more brute–force: a hard fork to mandate post–quantum crypto across the board. This would be simpler in execution (just change the rules at block X so that only PQ signatures are valid going forward), but politically and practically it’s far harder. Hard forks can split the chain if not everyone agrees – think of Bitcoin Cash splitting off in 2017 over a disagreement.
If a significant minority of users or miners refuses a quantum–hard–fork (perhaps because they disagree on timing or algorithm choice), you could end up with two competing Bitcoins, which would be a nightmare for value and trust. So, most see a hard fork for quantum as a last resort, perhaps only if an emergency dictates it and there’s near–unanimous consent out of sheer necessity.
We should also consider the user aspect: ordinary Bitcoin holders would need to move their coins to new addresses at some point to be safe. As long as they have their private keys, they can always spend from an old address into a new one. But some coins are lost or held by people who aren’t paying attention. Those coins might remain forever in vulnerable addresses.
One proposal (floated academically) is that if quantum computing arrives and some coins haven’t moved, there could be a “vaulting” or recovery process to protect them (perhaps miners temporarily freeze obvious quantum–theft attempts or something). However, that gets into very contentious territory of potentially violating Bitcoin’s fungibility or allowing special cases, which the community would be loath to do. Realistically, if someone doesn’t upgrade their coins after years of warning and then they get stolen by a quantum attacker, it would just be part of the fallout.
It’s worth mentioning that Ethereum and other smart contract platforms face a similar governance challenge. Ethereum’s culture is more open to upgrades (they hard–fork regularly for improvements), so it might execute a quantum–safe transition faster if needed. There’s even the possibility of using Ethereum’s programmability to allow both old and new signature types to coexist until a cutoff.
Some altcoins like Nano, Stellar, etc., use different signature schemes (like ed25519) which are equally vulnerable to quantum, so they’d need upgrades too. It’s a broad ecosystem issue. Coordination across chains isn’t strictly necessary (each network can handle itself), but imagine the scenario where one major coin goes PQ and others haven’t yet – there could be market shifts and arbitrage around perceived security.
In short, migrating a cryptocurrency to quantum–safe crypto is as much a social process as a technical one. It requires developers to write the code, yes, but then also miners to adopt it, businesses to update their systems, wallet providers to create user–friendly tools (so people can convert their funds to new addresses easily), and exchanges to recognize the new address formats. It’s a multi–year effort. The governance challenge is keeping everyone aligned and moving roughly in step rather than fracturing.
So far, Bitcoin’s community has shown it can rise to challenges when truly needed (e.g., the response to bugs or scalability issues), though not without drama. The looming quantum threat might actually serve as a unifying issue – nobody in crypto wants to see the coins broken. As long as the timeline is understood, one would hope even usually feuding factions of the community would come together to defend their collective interest: the integrity of the network.
Winners, Losers, and Economic Consequences
What would the crypto landscape look like if quantum computing reached the point of breaking contemporary encryption? It’s a scenario that could produce some clear winners and losers, at least in the short term, and broadly shake economic confidence in digital assets.
First, let’s consider the worst–case event: a sudden quantum attack becomes feasible and is unleashed on an unprepared network like Bitcoin. The immediate loser would be trust. Confidence in the security of cryptocurrency could evaporate overnight. Prices of major coins would likely plummet as holders scramble to sell before their funds get stolen. Remember, Bitcoin’s market cap (and that of other cryptos) is not just held by cypherpunk hobbyists anymore; it’s held by hedge funds, ETFs, companies like Tesla, and even nation–states (El Salvador, for one).
A collapse in Bitcoin’s price triggered by a security failure could send shockwaves through traditional markets as well, given the growing institutional exposure. We might see a broader financial contagion if, say, big investors have to write down crypto holdings or face liquidity issues. Panicked sell–off is the phrase that comes to mind.
In that chaos, who would be the “winners”? Obviously, the attacker (if it’s an entity) gains potentially massive amounts of stolen crypto – but spending it or cashing out may be tricky if everyone’s watching the addresses and exchanges blacklist the stolen funds. More interestingly, any assets or projects that are quantum–resistant could suddenly be in high demand. For instance, a niche coin like QRL (Quantum Resistant Ledger) might surge as people flock to something they perceive as safe. Companies offering post–quantum encryption solutions could see a boom in business (their services needed to secure exchanges, wallets, etc.). It’s also possible that alternative stores of value like gold or fiat currencies might get a relative boost as crypto temporarily loses shine.
However, longer term, the term “winners” is hard to assign because if confidence in cryptography is broadly shaken, everyone is in trouble. As cryptographer Michele Mosca warned, if quantum cracked our cryptosystems unexpectedly, “confidence in digital infrastructures would collapse.”
We’d shift from orderly migration to “crisis management,” which “won’t be pretty,” he said. That extends beyond crypto: think of secure communications, banking, the internet. So one could argue the only real winners would be those who foresaw it and prepared, thus avoiding disruption. Among crypto players, that could mean communities that upgraded in time or designed with quantum in mind from the start.
Let’s entertain a scenario where Bitcoin, through great effort, manages to migrate smoothly to post–quantum crypto before a quantum attacker arrives. In that case, Bitcoin’s network might sail through the “quantum scare” era and come out the other side robust. Its value proposition would actually strengthen (“Bitcoin survived the quantum transition!” would be quite the headline). Late–upgrading or stagnant projects could lose out. For example, if Bitcoin upgrades and some Bitcoin forks or smaller coins do not, users would likely abandon the weaker ones. One could imagine an investor rotation: moving capital from any coin perceived as lagging in quantum safety into those leading the pack. It’s a bit like Y2K for finance – companies that fixed their software in time were fine; those that ignored it risked failure.
We also have to consider the possibility of government intervention. If a quantum crisis hit, regulators might step in harshly. They could temporarily halt trading on crypto exchanges (to prevent further losses), or even attempt to coordinate a global response – perhaps pushing a certain standard upgrade quickly. Governments that were already skeptical of crypto might use the incident as fodder: “See, this stuff wasn’t safe, and now look at the mess.” On the flip side, if the crypto community navigates the quantum challenge well, it could impress regulators about the industry’s maturity and resilience, potentially building trust.
What about decentralized finance (DeFi) and smart contracts? Those systems rely on the underlying blockchain security. If Ethereum’s cryptography were compromised, for instance, all those DeFi contracts could be drained by quantum attackers forging transactions or stealing keys to multisigs. The entire DeFi ecosystem could unravel very fast – essentially a series of bank runs as every user tries to pull funds out before attackers do. Collateral values would plunge, liquidations cascade. It would make the DeFi hacks we’ve seen so far (usually due to bugs or key thefts) look minor by comparison. Again, projects that are proactive – say a lending platform that migrates to quantum–safe authentication for user withdrawals or a DEX that uses quantum–resistant keys for its admin controls – would fare better.
It’s worth noting some might find a silver lining or opportunity. For instance, crypto miners: if somehow only a few parties have quantum tech for mining, they could reap outsized rewards (until difficulty adjusts or the network responds). But realistically, if mining was dominated by a quantum computer, that chain is effectively broken because decentralization is gone. So that’s not so much a winner as a Pyrrhic victory for one entity.
Another angle: The insurance industry could face payouts if any insurers covered crypto losses due to theft (though many exclude such events). Alternatively, this could create a new market for “post–quantum insurance” and security services.
Economically, a quantum event hitting crypto could temporarily diminish the value of the whole sector – possibly by trillions in lost market cap in a severe scenario. But human ingenuity doesn’t stop. If people still see utility in cryptocurrency (and they likely will – the need for decentralized value exchange won’t vanish), the industry will rebuild on new, stronger foundations. Perhaps we’d see “Crypto 2.0” narratives with fully quantum–secure blockchains and maybe even quantum technology harnessed for new features. In summary, in a quantum disruption:
- Losers: Anyone holding unprotected crypto (which is most of us, currently), exchanges and financial institutions entangled with a falling market, and generally trust in the system. Also, technically, quantum computing companies might face backlash for unleashing chaos, though they’d also have a boom in interest for solutions.
- Winners: Those who hedged by investing in PQC early, quantum–resistant projects, possibly early adopters of upgraded coins, and the attackers (if malicious) until they get caught or their loot is rendered worthless by emergency forks or blacklisting.
In the long run, the biggest winner could be the crypto ecosystem if it adapts successfully – because it will have demonstrated adaptability and gained a new lease on life under the most serious threat to date. The process of getting there, however, could be economically tumultuous. The old saying, “An ounce of prevention is worth a pound of cure,” rings especially true here. By investing in prevention (upgrading algorithms, practicing good key hygiene like not reusing addresses, etc.), the crypto community can save itself from having to attempt an after–the–fact cure, which would be far more painful.
Quantum–Ready Projects and Future Outlook
Looking ahead, the intersection of quantum computing and crypto is as much an opportunity as it is a threat. It’s prompting a wave of innovation and investment in making cryptographic systems more robust. We’ve already highlighted some projects (QRL, Naoris, Quranium) that market themselves as quantum–ready. These might be considered niche now, but they offer a glimpse of how a post–quantum crypto ecosystem could function.
For example, QRL’s use of XMSS hash–based signatures means that even if a quantum computer existed, it couldn’t easily forge transactions on QRL – the security relies on cryptographic hash functions, which are relatively safer against quantum attacks (only affected by Grover’s algorithm’s quadratic slowdown). Similarly, Quranium’s use of stateless hash–based signatures (likely similar to SPHINCS+) means no reliance on classic elliptic curves or RSA at all.
In the broader industry, we’re seeing increasing funding for post–quantum cryptography startups and research groups. The U.S. and its allies have formed initiatives like PQCrypto to guide the adoption of new standards. The EU has its own projects under Horizon funding for quantum–safe cryptography. Venture capital is also interested: companies developing quantum–safe VPNs, secure messaging, or blockchain applications have begun to raise money, anticipating that demand will skyrocket as we inch closer to practical quantum computing. It’s analogous to the early days of cybersecurity – those who build the “quantum firewall” first could reap big rewards.
Interestingly, some blockchain projects are even looking at how quantum computing could be beneficial. For example, there’s speculative research on whether quantum computers could one day be used to run certain proof–of–work algorithms more efficiently (though that’s typically seen as a threat, not a benefit, as it centralizes mining). Another potential positive use: truly random number generation. Quantum processes are inherently random, so some protocols might use quantum random number generators to enhance unpredictability in consensus or cryptographic protocols (Cardano’s team has mentioned using quantum RNG for better randomness in leader election, for instance).
Moreover, if quantum computers eventually can solve optimization problems or simulate chemistry efficiently, blockchain networks focused on those fields (like networks for computing or science) might integrate quantum computing as part of their ecosystem (think oracles or off–chain computation that plug into smart contracts).
For everyday crypto users, the future outlook doesn’t require panic, but it does call for awareness and readiness. One practical step users can take today: avoid reusing addresses. As Nic Carter emphasized, basic hygiene like not using the same Bitcoin address repeatedly helps ensure your public key isn’t left out in the open longer than necessary. That way, even if a quantum computer came out tomorrow, it could only target you if you’ve done a transaction and exposed your pubkey; if your coins are sitting in an address that’s never been spent from, they’re a bit safer (until you spend them). In the future, wallets will likely start offering quantum–safe address options.
We might see, for instance, a Bitcoin wallet that can create a P2QRH address (should that BIP–360 plan or similar go through) and help you migrate your funds with a click. As a user, staying updated on these developments is key. There may come a day when you see a prompt: “Upgrade your wallet to quantum–resistant addresses now.” It would be wise to do so rather than procrastinate.
Another way users can “future–proof” their crypto holdings is by diversifying slightly into assets that are inherently quantum–proof. This could mean holding some coins on quantum–safe blockchains, or even holding assets that are not digital at all (as a hedge). However, given enough lead time, it’s likely that the major cryptocurrencies will handle the upgrade, so one shouldn’t have to abandon ship to remain safe.
From a community standpoint, expect to see a lot more collaboration between cryptographers, blockchain developers, and quantum physicists in the coming years. The problem crosses disciplines. We’ll likely see workshops and hackathons specifically on blockchain and post–quantum security. IEEE, IACR, and other bodies have already been fostering such cross–talk. This interdisciplinary effort is crucial because implementing PQC into a blockchain involves both understanding new math and adapting it to real–world network conditions.
Finally, the future outlook includes a scenario where quantum computers do arrive and crypto doesn’t just survive but thrives. If blockchains successfully transition to quantum–resistant algorithms, they might actually gain credibility. They will have passed one of the hardest possible tests of durability. And then, intriguingly, the door opens to quantum–powered cryptography. For example, zero–knowledge proofs and other advanced protocols could potentially be enhanced with quantum tech (there’s theoretical work on quantum zero–knowledge proofs).
We could even imagine blockchains one day securing themselves through quantum techniques like quantum entanglement–based consensus (far–fetched, but conceptually interesting: e.g., could quantum communications synchronize nodes with new guarantees?). These are far–out ideas, but they show that quantum computing isn’t just a threat vector – it could also be an enabler of new kinds of cryptographic trust if harnessed.
In summary, the crypto community is gearing up for the “quantum inevitable” in a proactive way. Emerging projects are leading the charge with quantum–proof designs, and major networks are slowly but surely mapping their migration paths. Users won’t need to understand the physics of qubits to benefit; they’ll just need to follow best practices and update their software as stronger protections become available. The arc of crypto has always been about resilience – from surviving exchange hacks, bear markets, regulatory crackdowns, and protocol bugs. The quantum challenge is another chapter in that story. It’s formidable, yes, but with early adaptation and global standards, the industry can not only prepare for this eventuality but come out stronger and more secure than before.
Final thoughts
Quantum computing and cryptocurrency exist on a collision course – maybe not today or tomorrow, but at some point in the future. The clash has often been framed in dramatic terms: “Quantum will be the end of Bitcoin.” Based on what we’ve explored, a more nuanced view is needed. Yes, quantum computers will one day break the specific cryptographic primitives that currently safeguard our digital assets. But that doesn’t have to mean the end of crypto or digital security. It means the beginning of a new chapter where we deploy stronger shields and perhaps even wield quantum tools for our defense.
Preparation is everything. The situation is reminiscent of the early days of the internet and the rise of cyber threats – those who recognized the risks of hackers and invested in cybersecurity thrived, while others learned the hard way. For the crypto sector, the lesson is clear: don’t be complacent. The goal is not to sow panic or sensationalize (we’ve hopefully avoided any alarmism here) but rather to emphasize a sober truth: we have a window of opportunity now to ensure that cryptocurrencies remain “unbreakable” even when quantum computers arrive that could otherwise break them.
That preparation will require global standards and collaboration. Just as NIST led a multi–year, international effort to vet post–quantum algorithms, the blockchain community may need its own equivalent – perhaps an alliance or working group that spans different projects, academia, and even governments, all aligning on quantum–resistant solutions for distributed ledgers. We might see something like a “Quantum–Safe Blockchain Alliance” emerge to share knowledge and coordinate timing, so that we don’t have a patchwork of some coins safe, others wide open, which could still lead to systemic issues.
It will also require a lot of education and communication. Developers must educate users on why certain upgrades are needed (we’ve seen how misunderstandings can slow down critical updates in the past). Communicating about quantum risks needs to strike a balance: not underplay the threat, but also not cry wolf too early such that people tune out. The messaging should be: This is an inevitable evolution in cryptography, and we have the solutions at hand – we just need to implement them with care and urgency.
One encouraging aspect is that many of the brightest minds in cryptography and computer science are already engaged in this problem. The coming transition to a post–quantum world is often likened to the transition from 32–bit to 64–bit computing, or from IPv4 to IPv6: a significant but manageable shift, given planning. In the best case, average crypto users in 2035 might not even remember that there was a quantum threat; they’ll just be using Bitcoin or Ethereum as usual, under the hood protected by lattice signatures or hash–based signatures, and life goes on. Achieving that “non–event” outcome will be the result of years of hard work happening right now (and perhaps some luck that quantum doesn’t arrive notably sooner than expected).
In concluding, it’s fitting to echo the sentiment that often comes from level–headed experts: don’t panic – prepare. Just as long–term Bitcoin holders think in terms of years and decades, the network’s security must be thought of in generational terms. Quantum computing is a once–in–a–century kind of technological shift. Navigating it will require interdisciplinary cooperation: cryptographers to design the algorithms, blockchain engineers to integrate them, business leaders to fund and implement them, and yes, quantum scientists to keep us informed about the true state of the technology (beyond the hype). This is not a challenge any one group can tackle alone.
The cryptographic cat–and–mouse game will continue as it always has. Quantum computers will force cryptography to evolve, and evolve it will. Blockchains, if they are to be the permanent fixtures of value exchange that many hope, must evolve too. In the end, the story of “unbreakable becomes breakable” might flip to “breakable becomes unbreakable again.” By getting ahead of the threat, the crypto community can ensure that its foundational promise – security without centralized trust – holds true, even against the most powerful computers humanity ever builds. The era of quantum computing will be an era of reckoning and then, hopefully, an era of renewal for crypto security. The time to start building that future is now.



