The cryptocurrency industry faces a fundamental tension: it was founded on principles of financial privacy and censorship resistance, yet operates in a world of increasingly stringent anti-money laundering (AML) and know-your-customer (KYC) regulations. This explainer examines how real cryptocurrency companies - exchanges, custodians, OTC desks, and payment processors - navigate this tension in their day-to-day compliance operations.
At the heart of modern crypto compliance sits a three-legged stool: KYC (identity verification at onboarding), AML (ongoing monitoring for suspicious activity), and KYT (Know-Your-Transaction tools that analyze blockchain data in real-time). Together, these create a compliance apparatus that would be familiar to any traditional financial institution, adapted for the unique challenges of pseudonymous, borderless, 24/7 crypto markets.
The stakes are extraordinarily high. Since 2020, global regulators have levied over $5 billion in fines against cryptocurrency firms for compliance failures. Binance's record $4.3 billion settlement with U.S. authorities in November 2023 showed that even the largest players face existential consequences for inadequate controls. Beyond financial penalties, compliance failures enable genuine harms: the Chainalysis 2024 Crypto Crime Report estimated $24.2 billion in illicit transaction volume across cryptocurrency in 2023, including ransomware payments, darknet market proceeds, and sanctions evasion.
This article provides an operational deep-dive into how compliance actually works. We examine the technology stack - particularly KYT tools from vendors like Chainalysis, TRM Labs, and Elliptic that power transaction monitoring. We explore what red flags trigger account freezes: interactions with sanctioned addresses, use of mixing services, unusual transaction velocity patterns, or geographic risk signals. We investigate how companies balance regulatory obligations with user privacy through techniques like minimal data collection, selective disclosure, and emerging cryptographic methods such as zero-knowledge proofs.
WHY COMPLIANCE MATTERS: RISKS, MONEY LAUNDERING, SANCTIONS, AND REPUTATIONAL COSTS
The Criminal Finance Problem
Cryptocurrency's pseudonymous nature and borderless transferability make it attractive for illicit finance. While the oft-cited claim that "most crypto is used for crime" is false - Chainalysis estimates illicit activity represented just 0.34% of all crypto transaction volume in 2023 - the absolute dollar amounts remain substantial and the use cases particularly harmful.
Ransomware operators have netted over $2 billion in cryptocurrency payments since 2020, with attacks crippling hospitals, schools, and critical infrastructure. The 2021 Colonial Pipeline attack alone resulted in $4.4 million in Bitcoin ransom (later partially recovered by the FBI). Darknet markets facilitate drug trafficking, with the now-defunct Silk Road, AlphaBay, and Hydra collectively processing billions in illegal goods sales. Terrorist financing, though representing a tiny fraction of illicit crypto use, carries severe consequences when discovered - exchanges that facilitate even inadvertent terrorist financing face potential criminal liability beyond civil penalties.
Sanctions evasion presents perhaps the highest-stakes compliance risk. The U.S. Treasury's Office of Foreign Assets Control (OFAC) maintains the Specially Designated Nationals (SDN) list, which includes cryptocurrency addresses associated with sanctioned entities. Notable entries include addresses tied to North Korea's Lazarus Group (responsible for the $625 million Axie Infinity Ronin Bridge hack), Russian darknet market operators, and Iranian entities. A single transaction touching a sanctioned address can trigger severe penalties: exchanges have faced multi-million dollar fines for processing transactions involving sanctioned users or addresses.
Regulatory Enforcement is Escalating
The past five years have seen a dramatic increase in enforcement actions:
-
Binance (2023): $4.3 billion settlement with DOJ, FinCEN, and OFAC for Bank Secrecy Act violations, unlicensed money transmission, and sanctions violations. Binance admitted to maintaining insufficient KYC controls, allowing transactions with users in sanctioned jurisdictions (Iran, Cuba, Syria), and deliberately evading U.S. regulations. CEO Changpeng Zhao pled guilty to criminal charges.
-
KuCoin (2024): $300 million settlement for operating as an unlicensed money transmitter and violating the Bank Secrecy Act. DOJ charged that KuCoin served U.S. customers without proper registration while neglecting KYC/AML obligations, processing billions in suspicious transactions.
-
BitMEX (2021-2022): $100 million in civil and criminal penalties for operating an unregistered trading platform and weak AML controls. Prosecutors noted BitMEX executives joked internally about regulatory evasion.
-
Bittrex (2022-2023): $53 million in combined penalties from OFAC and FinCEN for sanctions violations and BSA failures, including processing transactions for users in sanctioned jurisdictions.
These enforcement actions share common themes: inadequate KYC onboarding allowing sanctioned users, insufficient transaction monitoring missing obvious red flags, and corporate cultures that prioritized growth over compliance. The message to the industry is clear: compliance failures carry existential consequences.
Reputational and Operational Risks
Beyond legal penalties, compliance failures create severe reputational damage. Following enforcement actions, exchanges routinely see:
- Banking relationship terminations as risk-averse financial institutions cut ties
- Delisting from fiat on-ramps as payment processors refuse service
- User exodus to competitors with better compliance records
- Regulatory restrictions limiting expansion to new markets
- Increased due diligence burden from remaining partners
The operational burden of remediation also escalates costs. Post-enforcement, companies often must implement court-ordered monitorship (external compliance oversight, typically 3-5 years), conduct lookback reviews (examining potentially thousands of historical accounts), and hire significant compliance staff increases - Binance reportedly hired over 500 compliance personnel following its settlement.
Why Compliance ≠ Surveillance
A common misconception equates compliance with mass surveillance. In reality, modern crypto compliance focuses on risk-based approaches, targeting resources on genuinely suspicious activity rather than monitoring every user equally. Effective compliance programs:
- Use transaction thresholds to focus monitoring on high-value, high-risk activity
- Implement tiered KYC based on account limits and activity types
- Apply machine learning to reduce false positives and analyst burden
- Respect data minimization principles, collecting only required information
- Offer transparent appeal processes for erroneous account actions
The goal is proportionate controls that address genuine illicit finance risks while preserving privacy for the vast majority of legitimate users.
BASICS: KYC, AML, KYT - DEFINITIONS AND HOW THEY CONNECT OPERATIONALLY

Know Your Customer (KYC)
KYC refers to identity verification procedures conducted when a customer opens an account. For cryptocurrency exchanges and custodians, KYC typically involves:
Basic KYC (Tier 1):
- Full legal name
- Date of birth
- Residential address
- Email and phone number
- Government-issued photo ID (passport, driver's license, national ID card)
- Selfie verification (to prevent ID fraud/stolen documents)
Enhanced KYC (Tier 2):
- Proof of address (utility bill, bank statement)
- Source of funds documentation
- Occupation and employer information
- Expected transaction volumes and patterns
- For businesses: corporate registration, beneficial ownership disclosure
Institutional KYC (Tier 3):
- Complete corporate structure with ownership charts
- Audited financial statements
- AML policy documentation
- Regulatory licenses where applicable
- Background checks on key principals
The KYC process uses identity verification vendors such as Jumio, Onfido, or Persona, which leverage document verification, biometric matching, and database checks against watchlists. Verification typically completes within minutes for straightforward cases but may require manual review for edge cases (damaged documents, rare ID types, name mismatches).
Anti-Money Laundering (AML)
AML encompasses the broader framework of laws, regulations, and procedures designed to prevent, detect, and report money laundering. Key components include:
Risk Assessment: Companies must conduct enterprise-wide risk assessments identifying their specific money laundering vulnerabilities based on customer types, geographies served, products offered, and transaction volumes.
Customer Due Diligence (CDD): Beyond initial KYC, ongoing due diligence involves periodic reviews of customer information, monitoring for changes in behavior or risk profile, and enhanced scrutiny for high-risk customers.
Transaction Monitoring: Automated systems scan all transactions against rules-based and behavioral analytics models to detect suspicious patterns indicative of money laundering.
Suspicious Activity Reporting (SAR): When suspicious activity is identified, companies must file SARs with financial intelligence units (FinCEN in the U.S., FCA in the U.K., etc.). These reports detail the suspicious conduct, parties involved, and transaction details.
Recordkeeping: Regulations require maintaining detailed records of customer identities, transactions, and compliance decisions, typically for 5-7 years.
Independent Testing: Annual audits by internal or external auditors verify AML program effectiveness.
In the U.S., the Bank Secrecy Act (BSA) and its implementing regulations form the core AML framework. Globally, the Financial Action Task Force (FATF) sets international standards through its 40 Recommendations, which most jurisdictions adopt.
Know Your Transaction (KYT)
KYT represents the crypto-specific evolution of transaction monitoring, leveraging blockchain transparency to analyze transaction patterns and counterparty risk in real-time. Unlike traditional finance where transactions are opaque to most participants, public blockchains allow anyone to trace fund flows, creating both opportunities and challenges for compliance.
KYT tools continuously scan blockchain transactions associated with customer addresses, checking:
- Direct exposure: Does this transaction directly involve a sanctioned address or known illicit entity?
- Indirect exposure: Does this transaction's counterparty have recent connections to high-risk sources?
- Behavioral patterns: Does this transaction fit unusual velocity, structuring, or layering patterns?
- Service risk: Does this transaction involve high-risk services (mixers, darknet markets, unregistered exchanges)?
Major KYT vendors include Chainalysis (market leader), TRM Labs (emphasizing investigation tools), Elliptic (strong in DeFi and NFT coverage), and CipherTrace (now part of Mastercard). These tools provide APIs that integrate into exchange systems, returning risk scores and alerts in real-time as deposits or withdrawals process.
How KYC, AML, and KYT Connect Operationally
These three elements form an integrated compliance system:
-
Onboarding: KYC verifies identity, establishing the customer's regulatory status (jurisdiction, sanctions screening, PEP status). This determines initial risk scoring and transaction limits.
-
Ongoing Monitoring: KYT continuously analyzes blockchain transactions, feeding behavioral data into broader AML monitoring systems. High-risk transaction alerts trigger compliance review.
-
Investigations: When alerts fire, analysts use KYC data (identity, stated purpose), KYT forensics (blockchain tracing), and AML context (historical behavior, similar accounts) to make risk decisions.
-
Reporting: Confirmed suspicious activity becomes a SAR, with KYC data identifying parties and KYT forensics documenting the transaction trail.
-
Account Actions: Based on risk findings, companies may restrict services (lower limits), freeze accounts pending investigation, or terminate relationships. KYC data supports required customer notifications and appeals.
The feedback loop is continuous: KYT findings may trigger enhanced KYC reviews, while KYC risk factors adjust KYT alert thresholds.
📊 QUICK EXAMPLE: KYT IN ONE MINUTE
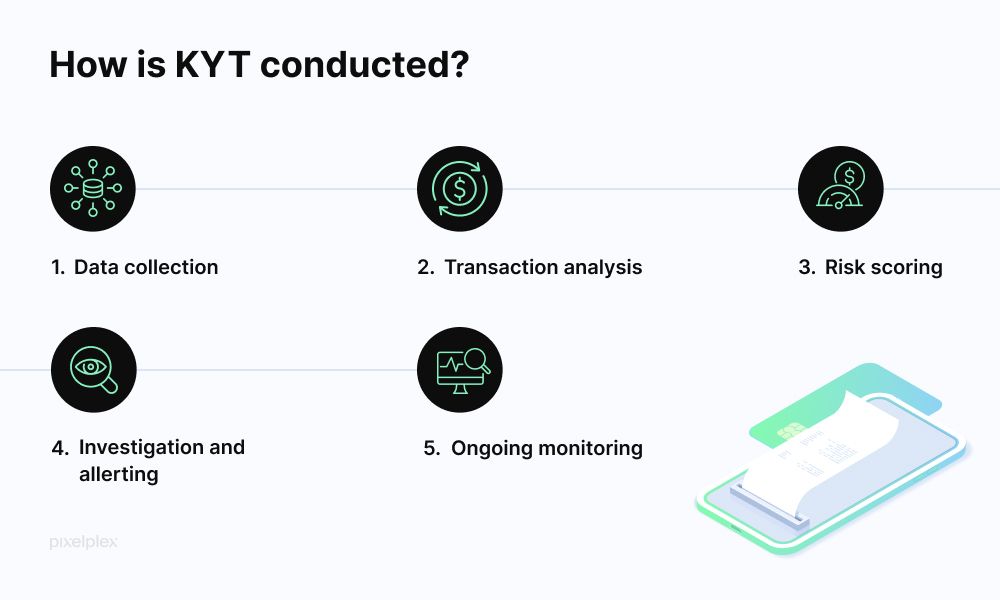
What is it? Know-Your-Transaction monitoring uses blockchain analysis to screen crypto transactions for illicit activity in real-time.
How does it work? Software continuously watches addresses linked to your account, checking every transaction against databases of known bad actors (ransomware wallets, sanctioned addresses, darknet markets). Each transaction receives a risk score based on direct and indirect exposure to risky counterparties.
Key difference from traditional finance: In traditional banking, your bank can't see what happens after you send money to someone else. With crypto, blockchain transparency lets KYT tools trace funds through multiple hops, following the money even after it leaves your account.
What triggers alerts? Direct contact with flagged addresses, use of mixing services, unusual patterns (many small deposits then one large withdrawal), connections to high-risk exchanges, or geographic red flags.
Privacy impact: KYT doesn't read your transaction "purpose" or personal messages. It analyzes on-chain patterns: amounts, timing, counterparty history, and service types. Your identity is only linked to transactions at regulated entry/exit points (exchanges, on-ramps), not on-chain.
COMPLIANCE OPS INSIDE EXCHANGES
Onboarding and KYC Flows
Modern centralized exchanges implement tiered verification systems balancing user friction with regulatory requirements and institutional risk tolerance:
Tier 0 - Unverified: Some exchanges allow limited functionality with just email registration - typically browsing markets, accessing educational content, or minimal test transactions. Most have eliminated this tier entirely under regulatory pressure.
Tier 1 - Basic Verification: Provides access to core trading with limits. Process typically requires:
- Government ID capture and verification (automated OCR plus liveness check)
- Sanctions screening against OFAC SDN, UN, EU sanctions lists
- PEP (Politically Exposed Person) screening
- Basic fraud checks (device fingerprinting, IP geolocation, email/phone validation)
Verification timing: 5-15 minutes for automated approval, 1-3 days for manual review cases. Typical limits: $2,000-$10,000 daily trading, smaller withdrawal limits.
Tier 2 - Enhanced Verification: For higher limits (often $50,000-$100,000 daily), additional requirements include:
- Proof of address (utility bill, bank statement, or tax document within 90 days)
- Source of wealth questionnaire
- Occupation and employer information
- Additional document verification (tax ID, social security number where applicable)
Tier 3 - Institutional/VIP: Custom limits with enhanced due diligence including:
- Video call verification with compliance team
- Detailed source of funds documentation
- Background checks on principals
- Ongoing relationship management with dedicated compliance contact
Transaction Monitoring and KYT Integration
Once onboarded, continuous monitoring begins. Exchanges integrate KYT tools at multiple points:
Deposit Screening: When cryptocurrency deposits arrive, KYT tools immediately analyze:
- Sending address history and known associations
- Path analysis: Where did these funds originate (potentially many hops back)?
- Direct risk: Any direct exposure to flagged entities?
- Indirect risk: Counterparties within 1-2 hops have risky associations?
- Service risk: Did funds pass through mixers, unregistered exchanges, darknet markets?
Risk scoring happens in seconds. Low-risk deposits credit immediately. Medium-risk deposits may credit with a delayed withdrawal hold pending review. High-risk deposits trigger immediate compliance team escalation, with funds potentially frozen pending investigation.
Withdrawal Screening: Before processing withdrawals, similar screening checks:
- Destination address risk
- Known associations of destination
- Customer's historical withdrawal patterns (is this unusual?)
- Velocity checks (has this customer moved through many small deposits and now wants one large withdrawal?)
Some exchanges conduct "pre-flight" checks, showing users a risk assessment before they confirm the withdrawal, allowing them to reconsider high-risk destinations.
Trade Monitoring: While less common than deposit/withdrawal screening, sophisticated exchanges also monitor trading patterns:
- Wash trading indicators (self-trading to fake volume)
- Market manipulation signals (pump and dump coordination, spoofing)
- Insider trading patterns (unusual pre-announcement accumulation)
- Account takeover signals (sudden strategy changes suggesting compromised account)
Escalation and Investigations Teams
When alerts fire, structured escalation protocols activate:
Level 1 - Automated Response:
- Low-severity alerts may auto-resolve if contextual data explains the pattern
- System may impose temporary limits (e.g., hold withdrawal for 24 hours) automatically
- Customer may see generic "additional verification required" messages
Level 2 - Analyst Review:
- Compliance analysts (typically requiring 6-12 months training) review flagged cases
- Analysis includes: KYC file review, blockchain forensics using KYT tools, checking similar historical patterns, reviewing customer communications
- Analysts can clear (no action), escalate (to senior staff), or impose controls (temporary freeze, permanent limits, account termination)
- Timeline: 1-3 business days for most cases
Level 3 - Senior Investigation:
- Complex cases involving significant amounts, potential sanctions violations, or criminal activity escalate to senior investigators
- May involve: extensive blockchain tracing, coordination with legal counsel, preparation of formal evidence packages
- May include: customer outreach requesting additional information, cooperation with law enforcement, filing SARs
- Timeline: 1-4 weeks or longer for complex cases
Level 4 - Executive/Legal Review:
- Highest-risk cases (major sanctions violations, law enforcement inquiries, potential criminal liability) reach executive level
- Decisions involve: Chief Compliance Officer, General Counsel, sometimes CEO
- Outcomes may include: immediate account termination, asset seizure and reporting to authorities, comprehensive lookback reviews for related accounts
Standard Operating Procedures (SOPs)
Leading exchanges maintain detailed SOPs covering common scenarios:
SOP Example - Mixer Exposure: If customer deposits funds with direct mixer exposure within 1 hop:
- Automatically hold deposit from crediting customer account
- Flag for Level 2 analyst review within 4 hours
- Analyst reviews: amount (over $1,000 = higher priority), customer history (first offense?), proportion of funds (10% from mixer vs. 90%?), customer risk tier
- If minor amount, first offense, small proportion: may approve with warning email to customer
- If significant amount or repeat pattern: escalate to Level 3, potentially freeze account and request customer explanation
- Document decision rationale in case management system
- If approved, retain enhanced monitoring flag for 90 days
SOP Example - Sanctions Screening Hit: If customer deposit includes any funds within 2 hops of OFAC SDN address:
- Immediate freeze of deposit, do not credit customer account
- Instant escalation to Level 3 senior investigator
- Within 2 hours: confirm hit is genuine (not false positive), determine proportion and recency of sanctioned exposure
- Within 24 hours: escalate to executive/legal review if genuine sanctions exposure
- Legal team determines: report to OFAC, file SAR with FinCEN, freeze all customer assets, prepare for potential asset seizure
- No customer communication until legal clears (avoid tipping off potential sanctions violator)
- If false positive: document analysis and release funds with apology to customer
Case Examples
Case 1 - The Innocent Mixer User: A customer deposited 0.5 BTC that KYT flagged as "high risk - recent mixer exposure." Investigation revealed the customer purchased the Bitcoin on a P2P platform (LocalBitcoins) from an individual seller. Unbeknownst to the customer, that seller had previously used a mixer. The compliance team determined: first offense, customer had no knowledge or control over prior history, relatively small amount. Resolution: Approved the deposit with an educational email to the customer about transaction screening and recommendation to use only regulated exchanges for purchases in the future. Enhanced monitoring applied for 60 days.
Case 2 - The Sanctions Evader: A customer using fabricated KYC documents (purchased identity) deposited funds eventually traced (6 hops back) to a darknet market. The customer made numerous small deposits over weeks, then attempted a large withdrawal to an address with direct ties to a sanctioned entity. Investigation found: VPN use masking true location, use of compromised identity, structured deposit pattern (staying below auto-review thresholds), destination with sanctioned exposure. Resolution: Account immediately frozen, all assets seized, SAR filed, customer information reported to law enforcement, internal review of verification procedures to identify control failure that allowed fake documents.
Case 3 - The False Positive: A customer received a deposit flagged as "medium risk - connection to unregulated exchange." Investigation revealed the funds came from a well-known decentralized exchange (Uniswap) through an aggregator service. The KYT vendor had incorrectly categorized the aggregator smart contract as "unregulated exchange." Resolution: Cleared the deposit within 4 hours, submitted feedback to KYT vendor to correct mislabeling, implemented whitelist for major DeFi aggregators to prevent future false positives.
Operational Metrics and Challenges
Volume Challenges: Large exchanges process millions of transactions daily. Even a 0.1% false positive rate means thousands of manual reviews. Industry benchmarks suggest:
- 0.5-2% of deposits trigger automated holds
- 0.05-0.2% escalate to human review
- 0.01% result in permanent account actions
Review Timelines: Most exchanges aim for:
- Low-risk alerts: automated resolution in seconds
- Medium-risk alerts: analyst review within 24 hours
- High-risk alerts: senior review within 48 hours
- Complex investigations: resolution within 5-10 business days
Staffing Requirements: Industry rule of thumb: 1 compliance analyst per $100-200 million in monthly trading volume, with 3-5 tier structure from junior analysts to senior investigators to legal counsel.
COMPLIANCE OPS INSIDE CUSTODIAL WALLETS & CUSTODIANS
Custodial service providers face additional compliance complexity beyond exchanges. Custody involves safeguarding customer assets (often with segregated cold storage), requiring additional controls around key management, withdrawal authorization, and client asset protection.
Custody-Specific Controls
Segregated Account Management: Custodians maintain separate wallets for each institutional client, preventing commingling that could complicate transaction screening or create liability in case of one client's compliance issues. This differs from exchanges that often use omnibus hot wallets, crediting customers through internal ledger entries.
Multi-Signature Authorization: Institutional custody typically requires multiple parties to authorize withdrawals:
- Client provides signed authorization (sometimes requiring multiple client employees)
- Custodian compliance reviews and approves
- Custodian operational team executes using multi-sig wallet
- All steps logged for audit trail
This creates compliance checkpoints: even if a client requests a withdrawal to a high-risk address, custodian compliance can block the transaction.
Enhanced KYT for Custodians: Custodians apply KYT differently than exchanges:
- They may not control the initial source of deposited funds (client manages their own incoming transactions)
- Primary focus is withdrawal screening, ensuring custodian doesn't facilitate transfers to sanctioned or high-risk destinations
- Emphasis on transaction policy enforcement (client-specific rules about approved destinations, velocity limits, notification requirements)
Disaster Recovery and Key Management: Custody compliance extends beyond AML to operational security:
- Secure key generation and storage (HSMs, multi-party computation, cold storage)
- Disaster recovery procedures ensuring client access
- Insurance and bonding requirements
- Regular proof-of-reserves and attestations
Custody KYC and Onboarding
Institutional custody clients undergo far more extensive due diligence than retail exchange users:
Initial Onboarding (4-8 weeks typical):
- Corporate structure verification (articles of incorporation, shareholder agreements, beneficial ownership disclosure)
- AML/KYC policy review (custodian evaluates client's own compliance program)
- Sanctions and negative news screening on entity and all key principals
- Financial review (audited statements, proof of legitimate business)
- Reference checks (contacting previous service providers)
- Legal documentation (custody agreement, fee schedules, liability limitations, insurance requirements)
- Technical onboarding (key generation ceremonies, access controls, recovery procedures)
Ongoing Monitoring:
- Annual re-verification of corporate documents and beneficial ownership
- Quarterly attestations from client regarding compliance status
- Continuous negative news monitoring
- Transaction pattern analysis (are withdrawals consistent with stated business purpose?)
Withdrawal Vetting Procedures
Before executing withdrawals, custodians conduct multi-layer review:
Pre-Authorization Stage:
- Client submits withdrawal request through secure portal
- Custodian verifies request authenticity (multi-factor authentication, callback verification for large amounts)
- System checks client account status (any holds, flags, or open issues?)
- System performs preliminary KYT screening on destination address
Compliance Review Stage:
- Analyst reviews KYT results on destination address
- Checks destination against client's approved destination list (many custody agreements restrict withdrawals to pre-approved addresses)
- Verifies withdrawal is consistent with client's stated activity (nature of business, expected patterns)
- For high-value transactions (often >$100,000), may require senior approval
- For highest-value (often >$1 million), may require executive approval
Execution Stage:
- Operations team verifies all approvals are in place
- Multi-sig authorization process executes transaction
- Real-time monitoring confirms transaction broadcasts correctly
- Post-transaction confirmation to client with full audit trail
Special Case - Law Enforcement Holds: If custodian receives legal process (subpoena, seizure warrant) regarding client assets, immediate freeze occurs. Custodian must balance:
- Legal obligation to comply with valid law enforcement requests
- Contractual obligation to client
- Potential liability if assets released improperly
- Client notification requirements (sometimes delayed by law enforcement)
Tradeoffs Specific to Custody
Client Privacy vs. Platform Compliance: Sophisticated custody clients (hedge funds, family offices) often value confidentiality regarding their holdings and trading strategies. Custodians must balance:
- Collecting sufficient information to satisfy their own compliance obligations
- Respecting client confidentiality
- Potentially refusing high-risk clients even if financially attractive
Operational Security vs. Velocity: Custody cold storage security (offline keys, geographic distribution, multi-party authorization) inherently creates friction:
- Withdrawal processing may take hours or days vs. seconds for exchange hot wallets
- This actually aids compliance (more time to review), but frustrates clients needing rapid access
- Some custodians offer "hot wallet as a service" for clients needing speed, but with lower balance limits and higher transaction monitoring
Insurance and Liability: Custodians face unique liability exposure:
- If custodian facilitates transaction to sanctioned destination, custodian faces enforcement action
- If custodian improperly blocks legitimate client transaction, faces breach of contract claims
- If custodian's security fails and assets stolen, faces negligence claims
- Comprehensive insurance is expensive but essential, and underwriters increasingly require robust compliance programs
Example: Qualified Custodian Requirements
In some jurisdictions (notably U.S. for RIAs managing >$150 million), investment advisers must use "qualified custodians" for client assets. For crypto assets, this means:
- Custodian must be a bank, broker-dealer, or registered trust company
- Must maintain adequate capital reserves
- Must undergo regular regulatory examinations
- Must provide account statements directly to clients
- Must have segregated client asset protection
These requirements significantly limit the custody provider landscape and impose additional compliance overhead, but provide stronger client protections.
COMPLIANCE OPS AT OTC DESKS AND LIQUIDITY PROVIDERS
Over-the-counter (OTC) trading desks facilitate large cryptocurrency transactions outside public orderbooks, primarily serving institutional clients, high-net-worth individuals, and other exchanges. OTC compliance differs meaningfully from exchange compliance due to client sophistication, transaction sizes, and direct counterparty relationships.
Client Vetting and Enhanced Due Diligence
OTC desks implement institutional-grade KYC that exceeds typical exchange requirements:
Initial Client Onboarding (2-6 weeks):
- Comprehensive corporate and personal background checks on all principals
- Financial statements and proof of funds source (particularly important for high-net-worth individuals)
- Understanding of business model and legitimate need for crypto exposure
- Investment thesis documentation (why are they trading crypto?)
- Expected volume and transaction frequency
- Banking relationships and traditional finance references
- Sanctions screening with enhanced review (OTC transactions often involve six-figure or higher amounts where even small proportionate sanctions exposure creates major risk)
Client Risk Tiering: OTC desks categorize clients:
- Tier 1 (Highest Trust): Regulated financial institutions, public companies, established hedge funds with strong compliance programs
- Tier 2 (Standard): Family offices, established high-net-worth individuals, crypto-native funds with audited financials
- Tier 3 (Enhanced Monitoring): Newer clients, those from higher-risk jurisdictions, or those lacking extensive documentation
Risk tier determines pricing (Tier 1 gets best rates), settlement terms (Tier 1 may get unsecured settlement, Tier 3 requires escrow), and monitoring intensity.
Trade Surveillance and Pre-Trade Compliance
Unlike exchanges where users trade independently, OTC desks execute trades on behalf of clients, creating compliance checkpoints at each stage:
Pre-Trade Screening:
- Client submits request (e.g., "Buy $5 million USDC for USD")
- Desk verifies client authorization (is the request authenticated?)
- Desk checks client account status (any flags, holds, or issues?)
- Desk verifies client has requisite funds/assets
- For cryptocurrency sells, desk conducts KYT screening on client's deposit addresses to ensure no tainted funds
If KYT screening finds high-risk source of funds, desk may:
- Decline the trade entirely
- Require additional documentation explaining source
- Offer reduced amount (clean portion only)
- Require client to use different funds
Trade Execution:
- Desk executes trade through various liquidity sources (exchanges, market makers, other OTC desks)
- Settlement occurs through established rails (wire transfer for fiat, blockchain transfer for crypto)
- Post-trade KYT screening on destination addresses (if client is receiving crypto, where are they sending it?)
Post-Trade Monitoring:
- Desk monitors client's subsequent use of cryptocurrency received
- If client immediately sends to high-risk destination (mixer, unregulated exchange, sanctioned address), desk may flag account for enhanced monitoring or restrict future transactions
- Unusual post-trade patterns might indicate client is intermediary for higher-risk end-user
Settlement Controls and Counterparty Risk
OTC desks face unique settlement challenges:
Escrow and DvP (Delivery versus Payment):
- For new or lower-tier clients, desk may require escrow settlement (third-party holds assets until both sides fulfill obligations)
- Atomic swaps or smart-contract-based DvP eliminates counterparty risk but adds complexity
- For Tier 1 clients, desk may extend unsecured settlement (trust-based), faster but requiring confidence in client
Sanctions Screening on Settlement: At settlement, final KYT checks occur:
- Desk verifies destination address hasn't been newly sanctioned (OFAC updates lists regularly)
- Checks no breaking news about client or their organization
- Verifies transaction details match agreed terms (amount, timing, addresses)
OTC-Specific Red Flags
Beyond typical exchange red flags, OTC desks watch for:
Layering Indicators:
- Client requests series of trades that seem designed to obscure source of funds (crypto to stablecoin to fiat to different crypto)
- Rapid reversal trades (buy then immediately sell)
- Use of multiple intermediaries or beneficiaries
Structuring:
- Client breaks large transaction into multiple smaller ones to avoid reporting thresholds
- Though less common in crypto (no direct equivalent to $10,000 CTR threshold), clients may try to avoid internal desk limits or enhanced scrutiny
Straw-Man Indicators:
- Client appears to be transacting on behalf of undisclosed principal
- Vague explanations about transaction purpose
- Mismatch between client profile (e.g., small business) and transaction size (e.g., $10 million crypto purchase)
- Client requests settlement to third-party addresses not previously disclosed
Geographic Risk:
- Client with legitimate business address requests settlement to addresses associated with high-risk jurisdictions
- Use of VPNs or privacy tools inconsistent with client's stated location
- Transactions routing through multiple jurisdictions unnecessarily
OTC Desk Operational Structure
Successful OTC desks maintain clear separation of duties:
Front Office (Trading): Client relationship management, price quotes, trade execution. Focused on client service and competitive pricing.
Middle Office (Compliance): Pre-trade approval, KYT screening, enhanced due diligence, ongoing monitoring. Reports independently of trading, can veto trades on compliance grounds.
Back Office (Settlement): Trade confirmation, asset movement, reconciliation. Final verification point before funds transfer.
Risk Management: Overall exposure monitoring, credit limit management, counterparty risk assessment. Works closely with compliance on high-risk situations.
This separation ensures compliance decisions aren't influenced by revenue pressure - a key control given that single OTC trades can generate five- or six-figure fees, creating strong incentives to overlook red flags.
HOW KYT TOOLS WORK: TECHNICAL WALKTHROUGH
Know-Your-Transaction tools represent the technological core of crypto compliance, translating blockchain transparency into actionable risk intelligence. Understanding how these tools work illuminates both their power and their limitations.
Data Sources and Collection
KYT vendors aggregate data from multiple sources to build comprehensive blockchain intelligence:
On-Chain Data (Primary Source):
- Full blockchain transaction history for supported chains (Bitcoin, Ethereum, and 100+ other networks)
- Vendors run full nodes, indexing every transaction, address, and smart contract interaction
- Data includes: transaction amounts, timestamps, sender/receiver addresses, gas fees, smart contract calls
- For Bitcoin: UTXO (unspent transaction output) tracking
- For Ethereum: account balances, ERC-20 token transfers, DeFi protocol interactions, NFT movements
Address Attribution (Labeling):
- Proprietary databases mapping addresses to real-world entities
- Sources include: public disclosures (exchanges publish deposit addresses), dark web intelligence (known ransomware wallets), law enforcement data sharing, investigative research, subpoena responses
- Chainalysis reportedly maintains labels for 500+ million addresses
- Categories include: exchanges (which exchange, sometimes which user), mixers/tumblers, darknet markets, gambling sites, sanctioned entities, ransomware operators, scams, DeFi protocols, mining pools
Sanctions Lists:
- OFAC Specially Designated Nationals (SDN) list with cryptocurrency addresses
- UN Security Council sanctions
- EU sanctions
- National sanctions (UK, Canada, Australia, Japan, etc.)
- Updates integrate within hours of official publication
Threat Intelligence:
- Monitoring dark web forums, Telegram channels, social media for emerging threats
- Tracking new scam patterns, compromised services, vulnerability exploits
- Intelligence on mixing techniques, chain-hopping patterns, new privacy tools
User-Submitted Reports:
- Crypto exchanges and other clients submit information about addresses they've identified as risky
- Creates network effect: more clients = better data = better service for all
Clustering and Attribution Methods
Raw blockchain data shows pseudonymous addresses, not identities. KYT tools use heuristics to cluster addresses into entities and attribute them to real-world actors.
Common Input Ownership Heuristic: When multiple addresses serve as inputs to a single Bitcoin transaction, they're likely controlled by the same entity (since the entity needs private keys for all inputs). Clustering algorithms group these addresses into wallets or entities.
Change Address Identification: Bitcoin transactions often create "change" outputs (leftover funds returned to sender). Identifying change addresses allows linking them to the sender's cluster.
Peel Chain Analysis: Tracking how funds move through sequential transactions, often seeing repeated patterns (spend small amount, return large change, repeat) that reveal fund flow paths.
Co-Spend Timing Analysis: Addresses frequently used together in short time windows likely belong to same controller.
Deposit Address Reuse: When exchanges reuse deposit addresses for same customer, this creates direct linkage to customer identity.
Smart Contract Interaction Patterns: On Ethereum, analyzing how addresses interact with DeFi protocols, following fund flows through DEX trades, lending protocols, bridges between chains.
Cross-Chain Tracking: Following assets as they bridge between blockchains (BTC wrapped to Ethereum, Ethereum bridged to Polygon, etc.). Requires correlating transactions on multiple chains, often using bridge protocol data.
Risk Scoring and Alert Generation
KYT tools assign risk scores based on multi-factor analysis:
Direct Exposure Scoring:
- Address has direct relationship with known-bad entity
- Severity varies: sanctioned entity = critical, unregulated exchange = medium, mixing service = high
- Most vendors use 0-100 or 0-1000 scale, with thresholds for auto-actions
Indirect Exposure Scoring:
- Funds came from risky source N hops away
- Risk decreases with distance: 1 hop = high risk, 2 hops = medium, 3+ hops = low
- Proportional weighting: 10% of funds from mixer = lower score than 90% from mixer
Behavioral Scoring:
- Transaction fits patterns associated with illicit activity
- Examples: structured deposits (many small instead of one large), rapid movement through multiple addresses, mixing service usage, layering through multiple cryptocurrencies
Counterparty Reputation:
- Is destination/source address associated with reputable entity?
- Sending to known legitimate exchange = low risk
- Sending to address with no history or recent creation = higher risk
Geographic and Compliance Risk:
- Does transaction involve addresses associated with high-risk jurisdictions?
- Does transaction involve service that lacks proper licensing?
Composite Scoring Example: Transaction receives final risk score combining:
- Direct exposure (40% weight): No direct risky contacts = 0 points
- Indirect exposure (30% weight): 2 hops from mixer = 30 points
- Behavioral (20% weight): Normal velocity, no structuring = 0 points
- Counterparty (10% weight): Destination is established exchange = 0 points
- Final Score: 9/100 = Low Risk
Different transaction:
- Direct exposure (40% weight): Direct deposit from mixer = 90 points
- Indirect exposure (30% weight): N/A when direct exposure present = 0 points
- Behavioral (20% weight): First deposit from this source = 20 points
- Counterparty (10% weight): Unknown address = 50 points
- Final Score: 76/100 = High Risk, triggers manual review
Alert Thresholds and Tuning
Customers configure KYT systems with thresholds matching their risk tolerance:
Conservative Configuration (Traditional Bank):
-
80/100 score = auto-block
- 50-80 = hold for manual review
- 30-50 = approve but flag for monitoring
- <30 = auto-approve
Moderate Configuration (Major Exchange):
-
90 = auto-block
- 70-90 = hold for review
- 40-70 = approve with monitoring flag
- <40 = auto-approve
Aggressive Configuration (Risk-Tolerant Platform):
-
95 = block (only direct sanctioned exposure)
- 85-95 = review
- All else = approve
Threshold Tuning Challenges:
- Too conservative = excessive false positives, customer friction, analyst overwhelm
- Too aggressive = miss genuine risks, regulatory exposure
- Optimal tuning requires continuous adjustment based on false positive rates, analyst feedback, and risk appetite changes
Real-Time vs. Batch Processing
Real-Time Screening (Deposit/Withdrawal):
- API call to KYT vendor as transaction processes
- Response time: 1-5 seconds typically
- Provides instant risk assessment before crediting deposits or executing withdrawals
- Handles: direct exposure checks, immediate clustering analysis, real-time sanctions list checks
Batch/Retrospective Analysis:
- Periodic (hourly, daily) review of all customer addresses
- Tracks: changes in risk profile (counterparty became sanctioned after you transacted), new intelligence linking old addresses to illicit activity, behavioral patterns emerging over time
- Can trigger: account reviews, enhanced monitoring flags, lookback investigations
Strengths of KYT Technology
Blockchain Transparency Advantage: Unlike traditional finance (where banks can't see counterparties beyond direct customer), blockchain analysis traces fund flows through unlimited hops, creating unparalleled transaction surveillance.
Speed and Scale: Automated analysis of millions of transactions daily, impossible with manual review.
Network Effects: More users submitting intelligence = better data for all = more accurate risk scoring.
Proactive Risk Identification: Can identify emerging threats (new scam addresses, newly sanctioned entities) and retroactively scan historical transactions.
Blind Spots and Limitations
Privacy Coin Challenges: Monero uses ring signatures and stealth addresses, making transaction amounts and participants cryptographically hidden. KYT tools have minimal visibility into Monero transaction details. Zcash with shielded transactions similarly obscures data. Vendors can track "shielding" and "unshielding" events (moving between transparent and private pools) but not activity within the shielded pool.
Mixing Service Evolution: As KYT tools improve at identifying mixer outputs, mixers adapt: using longer chains, more varied patterns, decentralized protocols (CoinJoin, TornadoCash-style smart contract mixers), cross-chain mixing. This creates ongoing cat-and-mouse game.
Decentralized Exchange Complications: DEX trades occur through smart contracts without centralized intermediaries. While on-chain, the transaction complexity makes attribution harder: is this address a trader, a liquidity provider, an arbitrage bot, or the DEX protocol itself?
Layer 2 and Rollup Challenges: Transactions on Layer 2 networks (Lightning Network, Arbitrum, Optimism) may not fully settle on-chain, reducing visibility. Lightning Network in particular creates off-chain payment channels with only open/close transactions visible on Bitcoin mainnet.
False Positive Rates: Industry estimates suggest 5-15% false positive rates even with tuned systems. Innocent users receiving funds from previously-tainted sources, good-faith transactions with legitimate privacy tools, or misattribution in clustering algorithms create compliance burdens and customer frustration.
False Negative Risks: Sophisticated actors can evade detection through: prolonged layering (many intermediate steps dilute tainted fund percentage), exploiting attribution gaps (new addresses, unmonitored chains), timing (allowing significant delay between illicit source and exchange deposit), or using privacy-preserving techniques KYT tools can't penetrate.
Labeling Accuracy Issues: Address labels depend on investigative research, which can be incomplete or incorrect. Addresses may be mislabeled (marking legitimate service as risky), or labels may become stale (address ownership transfers, service changes business model).
Comparative Vendor Analysis
Chainalysis (Market Leader):
- Strengths: Largest address database, strongest law enforcement relationships, most comprehensive blockchain coverage (200+ assets)
- Products: KYT (transaction monitoring), Reactor (investigation tool), Kryptos (asset recovery for law enforcement)
- Pricing: Enterprise licensing typically $100,000-$500,000+ annually depending on transaction volume
- Unique features: "Travel Rule" compliance tools, advanced investigation workflows, government partnerships
TRM Labs (Investigation Focus):
- Strengths: Superior investigation UI, real-time attribution updates, strong DeFi protocol coverage
- Products: TRM Chain (monitoring), TRM Forensics (investigations), TRM Screen (sanctions screening)
- Pricing: Competitive with Chainalysis, emphasizes value for smaller/mid-size customers
- Unique features: "Cross-chain tracing" through bridges and wrapped assets, TRM Risk API for developers
Elliptic (DeFi and NFT Specialty):
- Strengths: Deep DeFi protocol coverage, NFT marketplace monitoring, comprehensive smart contract risk analysis
- Products: Elliptic Navigator (monitoring), Elliptic Discovery (investigations), Elliptic Lens (wallet screening)
- Pricing: Range similar to competitors
- Unique features: DeFi risk scoring, NFT provenance tracking, "Instant Screening" SDK for developers
CipherTrace (Now Mastercard):
- Strengths: Traditional finance integration through Mastercard, strong global regulatory intelligence
- Products: CipherTrace Armada (platform covering monitoring and investigations)
- Unique features: Integration with Mastercard's broader financial crime tools, focus on bank/TradFi partnerships
Smaller/Specialized Vendors:
- Merkle Science: Asia-Pacific focus, strong compliance automation
- Coinfirm: European emphasis, MiCA compliance focus
- AnChain.AI: AI/ML-driven approaches, DeFi focus
- Scorechain: Privacy-focused approach, GDPR-compliant EU operations
Integration Architecture
Exchanges and crypto companies integrate KYT through several patterns:
API Integration (Most Common):
- Exchange systems call KYT vendor API on each transaction
- Request includes: blockchain, transaction hash or address, amount
- Response includes: risk score, risk factors, recommended action
- Typical latency: 1-3 seconds
Batch Upload:
- Exchange provides list of addresses to monitor
- Vendor continuously monitors these addresses, pushing alerts when risky activity detected
- Suitable for ongoing monitoring vs. real-time screening
On-Premise Deployment:
- For very large exchanges or those with data sovereignty requirements
- Vendor provides software installed on exchange's infrastructure
- Exchange maintains direct blockchain node connections
- Reduces latency and data sharing but increases operational burden
Hybrid Approach:
- Real-time API for immediate screening (deposits/withdrawals)
- Batch monitoring for ongoing surveillance
- On-premise investigation tools for compliance team
RED FLAGS THAT FREEZE ACCOUNTS: PRACTICAL LIST AND EXAMPLES
Understanding what triggers account freezes helps both companies implement effective monitoring and users avoid inadvertent problems. Red flags fall into several categories based on the underlying risk typology.
1. Direct Sanctioned Address Interaction
Description: Transaction directly involves an OFAC-sanctioned address or entity on other sanctions lists.
Severity: Critical - typically results in immediate freeze and regulatory reporting.
Examples:
- Receiving funds from an address on OFAC's SDN list (e.g., addresses associated with Lazarus Group, Russian darknet markets, Iranian entities)
- Sending funds to a sanctioned address
- Acting as intermediary in chain involving sanctioned addresses
Thresholds: Zero tolerance - any amount triggers action.
Real Case: In 2022, following the Tornado Cash sanctions, several users had accounts frozen at major exchanges after historical Tornado Cash usage, even if the usage predated sanctions designation.
2. Mixing and Tumbling Services
Description: Use of cryptocurrency mixers (CoinJoin, Wasabi Wallet, Samourai Whirlpool) or tumblers designed to obscure transaction history.
Severity: High to Critical depending on proportion of funds and customer history.
Examples:
- Depositing funds where >50% recently passed through Tornado Cash
- Withdrawal to known Wasabi CoinJoin address
- Pattern of consistently using privacy-enhancing tools
Thresholds:
- Conservative platforms: >10% mixer exposure triggers review
- Moderate platforms: >25% mixer exposure requires review
- Many platforms: Direct mixer usage (deposit from or withdrawal to) = automatic hold
Real Case: User deposited Bitcoin to exchange after running funds through Wasabi Wallet CoinJoin. Exchange froze account pending explanation. User provided documentation showing funds were legitimately earned but wanted privacy from public blockchain exposure. Exchange required additional KYC documentation and source of funds proof before releasing.
3. Darknet Market and Illicit Service Linkage
Description: Funds traced to darknet marketplace, illegal gambling site, unlicensed exchange, or other clearly illicit services.
Severity: Critical - strong indicators of money laundering or direct criminal activity.
Examples:
- Deposits traced within 2-3 hops to AlphaBay, Hydra, or similar marketplaces
- Funds from addresses associated with ransomware payments
- Connections to known scam addresses (pig butchering schemes, Ponzi schemes)
Thresholds:
- Direct connection (1 hop): Immediate freeze regardless of amount
- Indirect connection (2-3 hops) with significant proportion (>25%): Review required
- Distant connection (4+ hops) with small proportion (<10%): May pass with monitoring flag
Real Case: User withdrew their exchange balance to a personal wallet, then several days later sent funds to a darknet market. Exchange's retrospective monitoring detected this, leading to account termination and SAR filing, even though the illicit activity occurred after funds left the exchange.
4. Rapid Movement and Layering Patterns
Description: Funds moving through multiple addresses, services, or cryptocurrencies in rapid succession, indicating potential layering stage of money laundering.
Severity: Medium to High depending on pattern complexity and amounts.
Examples:
- Deposit of BTC → immediate conversion to ETH → immediate withdrawal to different service
- Funds that bounced through 10+ addresses in 24 hours before depositing
- Pattern of receiving many small deposits from different sources, then one large withdrawal ("convergence pattern")
Thresholds:
- 5+ hops in 48 hours before deposit: Triggers review
- Immediate convert-and-withdraw with no trading: Medium risk flag
- Structured patterns with <$10,000 individual transactions but >$50,000 aggregate: High risk
Real Case: User received 15 deposits of 0.1-0.3 BTC each over three days from different addresses, then immediately requested withdrawal of entire balance. Exchange froze account suspecting money mule activity. Investigation revealed user was Bitcoin miner consolidating mining pool payouts - legitimate but suspicious pattern. Resolved with documentation of mining activity.
5. Structured Deposits ("Smurfing")
Description: Breaking large transactions into multiple smaller ones to avoid reporting thresholds or risk scoring triggers.
Severity: Medium to High - indicates awareness of monitoring systems and potential attempt at evasion.
Examples:
- 10 deposits of $900 each (staying below $1,000 threshold) over 24 hours
- Pattern of consistent near-threshold deposits ($9,500 repeatedly when $10,000 triggers CTR)
- Multiple accounts controlled by same person splitting activity
Thresholds:
- Automated systems typically flag: 3+ transactions within 20% of threshold amount in 24 hours
- Advanced systems use statistical analysis to detect intentional structuring vs. natural patterns
Real Case: Family splitting large Bitcoin purchase across three family member accounts to each stay under enhanced KYC threshold. Exchange detected common funding source (same bank account) and linked accounts. Required explanation and consolidated accounts under one primary user with proper KYC.
6. High-Risk Jurisdiction Indicators
Description: Activity associated with jurisdictions identified as high-risk for money laundering, terrorist financing, or sanctions evasion.
Severity: Low to High depending on jurisdiction, customer profile, and transaction details.
Examples:
- Deposits from addresses associated with Iranian or North Korean services
- VPN usage masking true location in sanctioned country
- IP addresses from Financial Action Task Force (FATF) blacklist countries
- Transactions routing through services headquartered in high-risk jurisdictions
Thresholds:
- FATF blacklist countries (e.g., North Korea, Iran): Typically blocked entirely
- FATF greylist countries: Enhanced monitoring, may require additional documentation
- IP/VPN from high-risk location with inconsistent KYC address: Investigation required
Real Case: User with U.S. KYC documents consistently accessed account through Iranian IP addresses. Exchange investigation revealed user was Iranian-American temporarily residing in Iran. Account frozen pending determination of sanctions implications, eventually terminated due to inability to verify user wasn't violating OFAC restrictions on Iranian nationals.
7. Peer-to-Peer Platform Linkage
Description: Funds originating from P2P platforms (LocalBitcoins, Paxful, Binance P2P) where KYC/AML controls may be weaker.
Severity: Low to Medium - often legitimate but higher risk due to unknown counterparties.
Examples:
- Deposit from address known to be LocalBitcoins trader
- Pattern suggesting user is P2P marketplace seller (many incoming transfers from different sources)
- Funds from unregulated or jurisdictionally ambiguous P2P platforms
Thresholds:
- Depends heavily on platform: well-regulated P2P = minimal concern, unregulated = medium risk
- First-time users with P2P source: Often require explanation and enhanced KYC
- Large amounts (>$10,000) from P2P: Review standard
Real Case: User deposited Bitcoin purchased on LocalBitcoins. KYT tools traced portion of funds to prior mixer use by the LocalBitcoins seller (unknown to user). Exchange requested user provide LocalBitcoins transaction records showing legitimate purchase and encouraged using regulated exchanges in future. Funds released after documentation provided.
8. Unregulated Exchange or Service Usage
Description: Interaction with cryptocurrency exchanges or services lacking proper licensing/regulation in relevant jurisdictions.
Severity: Low to High depending on platform reputation and regulatory environment.
Examples:
- Deposits from exchange operating without registration in user's jurisdiction
- Withdrawals to platforms with known compliance deficiencies
- Funds transiting through exchanges serving sanctioned jurisdictions
Thresholds:
- Exchanges with serious compliance failures (binance.com during pre-settlement period): High risk
- Offshore exchanges with minimal regulation: Medium risk
- Legitimate exchanges with presence in user's jurisdiction: Low/no risk
Real Case: During peak of 2021 bull market, user withdrew funds to newly-launched exchange with minimal KYC requirements. Original exchange flagged destination as "unregulated," but allowed withdrawal with warning to user about counterparty risk. Six months later, destination exchange was hacked and user lost funds - original exchange's warning provided legal protection in subsequent user complaints.
9. Velocity and Volume Anomalies
Description: Transaction patterns inconsistent with user's historical behavior or stated account purpose.
Severity: Low to Medium - often legitimate (market conditions, life changes) but requires explanation.
Examples:
- Account averaging $1,000 monthly volume suddenly processes $100,000
- User who claimed "long-term holding" suddenly making dozens of daily trades
- Dormant account suddenly activated with large deposits and immediate withdrawals
Thresholds:
- 10x increase in usual volume: Automated review trigger
- Activity inconsistent with stated account purpose: May require re-verification
- Sudden activation after >6 months dormancy with large transactions: Enhanced monitoring
Real Case: Long-dormant account received $75,000 Bitcoin deposit and immediately requested withdrawal to external wallet. Exchange froze account suspecting compromise. User verification confirmed legitimate ownership - user had forgotten about account, rediscovered seed phrase, and was consolidating holdings. Account unfrozen after identity reverification.
10. High-Risk Counterparty Indicators
Description: Transacting with addresses or entities known to have poor compliance controls or high-risk activity.
Severity: Low to High depending on counterparty risk profile.
Examples:
- Sending funds to gambling sites (especially in jurisdictions where illegal)
- Deposits from ICO projects that failed to conduct proper KYC
- Transactions with addresses involved in mass unsolicited transfers ("dust attacks")
Thresholds:
- Regulated gambling (licensed jurisdictions): Typically acceptable
- Unregulated or illegal gambling: Medium to high risk
- Known scam or fraudulent projects: Immediate flag
Practical Threshold Examples from Industry
Conservative Institutional Exchange (Coinbase, Gemini, Kraken):
- Direct sanctioned exposure: Instant freeze
-
15% mixer/tumbler exposure: Hold pending review
-
3 hops from darknet market: Review required
- Structuring patterns detected: Automatic escalation
-
$25,000 from P2P platforms: Source of funds requested
Moderate Exchange (Binance.US post-settlement, Crypto.com):
- Direct sanctioned exposure: Instant freeze
-
40% mixer exposure: Hold pending review
-
2 hops from clear illicit service: Review
-
$50,000 unexplained velocity increase: Monitoring flag
- Withdrawal to high-risk destination: Warning but allowed (user assumes risk)
Risk-Tolerant Platform (Historical Binance.com pre-2023, smaller exchanges):
- Direct sanctioned exposure only: Freeze
- Mixer exposure: Generally allowed unless >80%
- Unregulated exchange usage: Accepted
- Emphasis on user responsibility over platform prevention
These thresholds constantly evolve based on regulatory pressure, enforcement trends, and institutional risk appetite.
PRIVACY TRADEOFFS AND MITIGATION TECHNIQUES
The tension between compliance requirements and user privacy represents perhaps the most contentious issue in cryptocurrency regulation. This section examines practical privacy-preserving approaches companies employ and their limitations.
Minimal Data Collection Practices
Tiered KYC Approach: Rather than requiring full identity verification for all users, some platforms implement graduated requirements:
- Level 0: Email only, browse markets, minimal deposits ($100-500)
- Level 1: Basic ID, moderate deposits ($5,000-10,000)
- Level 2: Enhanced verification, high limits ($50,000+)
- Level 3: Institutional full due diligence, unlimited
This allows users needing limited services to maintain greater privacy while reserving intensive verification for high-value activities.
Data Minimization: Collect only information genuinely required for compliance, not "nice to have" marketing data:
- Don't require employment details unless regulatory requirement
- Don't store full document images longer than necessary for verification
- Don't collect browsing history, transaction purposes, or counterparty relationships beyond blockchain-visible data
- Implement data retention policies (delete after X years if no regulatory hold)
Segregated Storage: Separate compliance-necessary data from other business systems:
- KYC data in access-controlled environment separate from marketing databases
- Blockchain analysis separate from personal identifying information (PII)
- Only compliance staff with justified need access PII
Pseudonymous User Experience
Address Rotation: Generate new deposit addresses for each transaction rather than reusing addresses. This limits blockchain observers' ability to aggregate user activity, even though the exchange internally links all addresses to the user's account.
Internal Settlement: When both sender and receiver use the same exchange, settle internally without blockchain transactions. This keeps transaction details off public ledger while maintaining full compliance internally.
Privacy-Preserving Interfaces:
- Don't publicly display user balances, transaction histories, or trading activity
- Implement privacy by default in UI/UX design
- Allow users to opt-in to public profiles rather than opt-out
Selective Disclosure and Attestations
Attestation-Based Verification: Rather than providing complete identity documents, users receive cryptographic attestations proving specific claims:
- "User is over 18" (without revealing exact birthdate)
- "User is not on sanctions list" (without revealing identity)
- "User resides in permitted jurisdiction" (without revealing exact address)
Third-party verification services issue signed attestations that platforms verify cryptographically without seeing underlying PII.
Reusable KYC Credentials: User completes KYC once with trusted verifier, receives portable credential, then presents to multiple services without repeating full process:
- Standards: W3C Verifiable Credentials, Decentralized Identifiers (DIDs)
- User controls: what information to disclose to which service
- Benefits: Reduced repeated data exposure, user privacy control, verification cost reduction
Implementation Challenges:
- Limited regulatory acceptance (most jurisdictions require direct verification)
- Credential revocation difficulties (how to revoke compromised credentials?)
- Trust framework needed (who are acceptable attestation issuers?)
- Technical complexity (wallet software, key management, credential standards)
Multi-Party Computation Approaches
Concept: Secure Multi-Party Computation (SMPC) allows multiple parties to jointly compute functions over their inputs while keeping inputs private. In compliance context, this could enable:
Cross-Platform Sanctions Screening: Multiple exchanges collectively check if address is sanctioned without revealing which exchange asks:
- Each exchange submits encrypted query
- Computation determines if address appears in any exchange's sanctions list
- Only boolean result revealed ("sanctioned" or "not sanctioned"), not which exchange flagged or why
Collaborative Fraud Detection: Platforms share fraud indicators without exposing customer details:
- Detect patterns across platforms (same fraudster working multiple exchanges)
- Preserve privacy of individual customer data
- Improve collective security
Current Limitations:
- Computational overhead (slower than plaintext operations)
- Complex implementation requiring specialized expertise
- Limited production deployments in crypto compliance
- Regulatory uncertainty (will authorities accept SMPC-based compliance?)
Zero-Knowledge Proof Applications
Core Concept: Zero-knowledge proofs let one party prove to another that a statement is true without revealing any information beyond the statement's truth.
Compliance Applications:
KYC Without Identity Disclosure:
- User proves "I completed KYC with trusted verifier X" without revealing identity to service Y
- User proves "My identity documents are valid and not expired" without showing documents
- User proves "I'm not on sanctions list" without revealing nationality or identity
Transaction Compliance:
- User proves "This transaction doesn't involve sanctioned addresses" without revealing full transaction graph
- User proves "My account balance exceeds $X" without revealing exact balance
- Platform proves to regulator "We screened all users" without providing user list
Research Implementations:
Aztec Protocol developed zk-rollup technology allowing private transactions while maintaining regulatory compliance through selective disclosure - users can prove transactions are legitimate without revealing details publicly.
Dusk Network implements "confidential security tokens" with built-in compliance: transactions are private on-chain, but include zero-knowledge proofs of regulatory compliance (KYC, accredited investor status, etc.).
Zcash supports "selective disclosure" where users can prove transaction details to specific parties (auditors, regulators) without public exposure.
Practical Constraints:
- Proving complexity: generating proofs requires significant computation
- Verification must be trustworthy: who verifies the ZK proofs are legitimate?
- Regulatory skepticism: authorities want ability to investigate, not just mathematical proof
- Limited production readiness: most ZK compliance systems are research-phase
- Key management risks: if ZK proving keys compromised, system security fails
Privacy Coin Risks and Mitigation
Privacy coins like Monero, Zcash (shielded), and Dash present unique compliance challenges and platform responses:
Complete Delisting: Many regulated exchanges no longer support privacy coins:
- Coinbase never listed Monero or shielded Zcash
- Kraken, Bittrex delisted privacy coins under regulatory pressure
- Australian exchanges required to delist privacy coins
Transparent-Only Support: Some exchanges support privacy coins but only transparent transactions:
- Zcash: only transparent (t-addr) deposits/withdrawals allowed, not shielded (z-addr)
- Prohibit shielding/unshielding within platform
- Treat shielded transaction exposure similar to mixer exposure
Enhanced Monitoring: Platforms supporting privacy coins implement stricter controls:
- Lower withdrawal limits for privacy coins
- Enhanced KYC requirements for privacy coin users
- Immediate manual review of privacy coin transactions
- Clear terms of service about privacy coin usage restrictions
Compliance Rationale: Regulators view privacy coins as inherently high-risk due to limited blockchain analysis ability. FATF guidance suggests privacy coins may be incompatible with travel rule compliance (cannot identify counterparties if transactions are private).
Risk-Based Decision Making
Successful privacy-respecting compliance requires thoughtful risk-based choices:
Risk Factors Considered:
- Customer risk: Individual retail vs. institutional, KYC quality, jurisdiction, historical behavior
- Product risk: Simple spot trading vs. complex derivatives, fiat on/off-ramp vs. crypto-only
- Transaction risk: Amount, counterparties, velocity, pattern
- Geographic risk: Operating jurisdictions, user locations, transaction routing
Risk-Based Controls:
Low-Risk Scenario (Retail user, small amounts, established relationship):
- Basic KYC sufficient
- Automated transaction screening
- Monthly pattern analysis
- Annual KYC refresh
High-Risk Scenario (Institutional client, large volumes, new relationship):
- Enhanced due diligence
- Manual pre-approval of significant transactions
- Continuous monitoring with tight thresholds
- Quarterly relationship reviews
- Dedicated compliance contact
Privacy Preservation Hierarchy:
- Collect minimum data required by regulation (not maximum possible)
- Use aggregated/anonymized data for analytics where possible
- Implement technical controls (encryption, access limits) for sensitive data
- Minimize data retention (delete when legally permissible)
- Provide transparency to users about data collection and usage
- Enable user control (data export, correction, deletion where legally allowed)
This risk-based approach allows companies to apply strict controls where genuinely needed while preserving privacy for lower-risk activities - balancing compliance obligations with user expectations.
LOOKING FORWARD: THE FUTURE OF COMPLIANCE AND PRIVACY IN CRYPTO
The cryptocurrency industry stands at a crossroads. The compliance infrastructure described throughout this article - KYC onboarding flows, KYT transaction monitoring, sanctions screening, risk-based investigations - has matured significantly since Bitcoin's early days. What began as an unregulated frontier now operates under increasingly robust frameworks that resemble, and in some cases exceed, traditional financial services compliance. Yet fundamental tensions remain unresolved.
Regulatory Trajectory: Convergence and Expansion
Global regulatory harmonization is accelerating. The FATF Travel Rule, requiring counterparty information exchange for transfers above $1,000, is being implemented across jurisdictions despite significant technical challenges. The EU's Markets in Crypto-Assets (MiCA) regulation, effective in 2024-2025, establishes comprehensive licensing, consumer protection, and AML requirements that will become the template for many other regions.
In the United States, agencies continue expanding enforcement - the SEC's ongoing cases against exchanges for unregistered securities offerings, the CFTC's derivatives jurisdiction assertions, and FinCEN's BSA enforcement all point toward tighter controls.
This regulatory convergence brings clarity but also costs. Compliance expenses at major exchanges now run into tens of millions annually: KYT vendor licenses, compliance staff salaries, technology infrastructure, legal counsel, and regulatory fees. These costs create consolidation pressures, favoring large, well-capitalized platforms over innovative newcomers. The decentralized ethos that attracted many to cryptocurrency confronts a reality where only institutional-scale operations can afford comprehensive compliance.
Technology Evolution: Privacy-Preserving Tools Maturing
Despite regulatory headwinds, privacy-preserving technology continues advancing. Zero-knowledge proof systems have progressed from academic curiosities to production deployments - Aztec, Aleo, and others demonstrate that privacy and compliance can coexist technically, even if regulatory acceptance lags. Selective disclosure credentials and verifiable credentials standards offer paths toward reusable KYC without repeatedly exposing identity documents. Multi-party computation schemes could enable collaborative fraud detection without compromising individual user privacy.
The question is whether regulators will accept these approaches. Historically, financial regulators have favored direct visibility over cryptographic assurances. Convincing authorities to accept zero-knowledge compliance proofs requires not just technical soundness but institutional trust-building, audit frameworks, and incident response protocols that satisfy government investigators. Early regulatory sandbox experiments in Switzerland, Singapore, and the UK may chart paths forward, but widespread adoption remains years away.
Industry Bifurcation: Regulated vs. Decentralized Ecosystems
The compliance-privacy tension is driving cryptocurrency into two increasingly distinct ecosystems:
- Regulated Platforms: Centralized exchanges, custodians, and payment processors operating as quasi-banks with full KYC/AML/KYT infrastructure, banking relationships, fiat on-ramps, institutional custody, and regulatory licenses. These platforms serve mainstream users prioritizing convenience, security, and legal clarity over absolute privacy
- Decentralized Alternatives: DEXs, non-custodial wallets, peer-to-peer protocols, and privacy tools serving users who prioritize censorship resistance and financial privacy. These alternatives face growing regulatory pressure - the Tornado Cash sanctions and subsequent prosecution of developers signals authorities' willingness to target even non-custodial privacy tools
- This bifurcation creates an uncomfortable reality: users must choose between regulatory protection (insurance, recourse, legal clarity) and financial autonomy (self-custody, privacy, permissionless access). The cryptocurrency vision of "be your own bank" remains technically possible but increasingly exists in tension with regulatory frameworks designed around intermediaries.
Practical Realities for Users and Companies
For individuals using cryptocurrency, the compliance landscape demands pragmatism:
- Understand that any interaction with regulated platforms creates permanent identity linkage and transaction surveillance
- Recognize that privacy tools, while legal in most jurisdictions, may trigger enhanced scrutiny or account restrictions
- Accept that most mainstream use cases (trading, custody, fiat conversion) currently require KYC concessions
- Research platform compliance practices before choosing services, balancing privacy preferences with regulatory risk tolerance
For companies building in the space, navigating compliance requires strategic choices:
- Licensing strategies determine where and how you can operate - balancing jurisdictional requirements with operational complexity
- Technology investments in KYT, case management systems, and investigation tools represent unavoidable costs of market access
- Compliance culture must be genuine, not performative - regulators increasingly prosecute companies whose compliance programs exist only on paper
- Risk tolerance calibration determines your market position: conservative approaches limit regulatory exposure but may sacrifice competitive advantages
The Unresolved Paradox
Cryptocurrency was built to enable financial transactions without trusted intermediaries, yet compliance by definition requires intermediaries who verify identities and monitor transactions. Smart contract platforms were designed to execute code unstoppably, yet regulators demand the ability to freeze assets and reverse transactions. Public blockchains create permanent transparent records, yet privacy remains a legitimate user expectation. These tensions have no simple resolution.
The compliance approaches detailed in this article represent pragmatic compromises: doing enough to satisfy regulators while preserving enough autonomy to remain recognizably "crypto." Whether these compromises prove sustainable depends on regulatory evolution, technological innovation, and ultimately, society's willingness to accept financial systems that operate differently than traditional banking.
The cryptocurrency industry's compliance maturation from 2020-2025 demonstrates that digital assets can coexist with regulatory frameworks. The question for 2025-2030 is whether they can do so while retaining the properties - permissionless access, financial privacy, censorship resistance - that made them compelling in the first place. That answer remains unwritten, shaped by ongoing contests between competing visions of financial freedom, security, and control.



